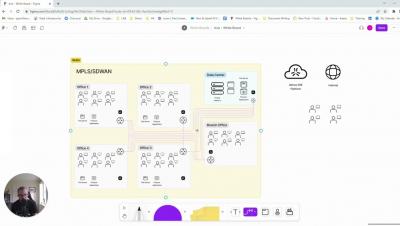
The ZTNA Evolution - My Journey
As many of you know, I was an early adopter of Zero trust Network Access (ZTNA) while working in my previous role, which led me to work at Axis today. As our contract was coming up for renewal, I did what all IT folks do and went out on the market to see what had changed during our contract period and to see if anything existed that was better.