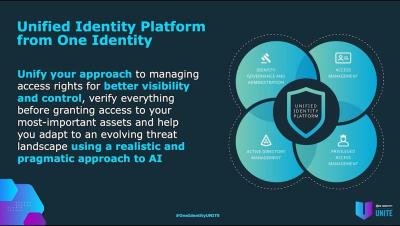
Six ways privilege management improves your security posture
Identities, computers and groups all need access to resources. But only enough to fulfill a role, and only for as long as they need it. AD Admins, IT leaders, VPs and CISOs recognize this as a foundational part of Zero Trust least privilege models – and as one of the biggest challenges for enterprises. That’s because using native tools for privilege management is complex.