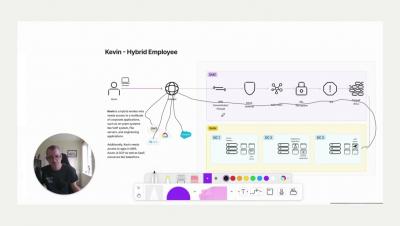
6 Examples of Discretionary Access Control (DAC)
As the basis of pretty much every consumer system available today, Discretionary Access Control (DAC) is everywhere and used by everyone. The files on your computer, the media and applications on your smartphone, and even your social media content. They all use DAC to manage permissions. That’s in part because DAC is easy to manage and understand. But DAC also has a few glaring issues when it comes to cybersecurity.