Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Git
Toyota data breach - Database keys exposed publically in GitHub for 5 years
[Webinar] DevOps backups vs. ransomware - best security and compliance practices.
[Webinar] DevSecOps - A DevSecOps Maturity Model for Secrets Management
The Uber Hack - A step by step breakdown of the 2022 Uber data breach
"Gitting" the Malware: How Threat Actors Use GitHub Repositories to Deploy Malware
The CrowdStrike Falcon Complete™ managed detection and response (MDR) team recently uncovered a creative and opportunistic interpretation of a watering hole attack that leverages GitHub to gain access to victim organizations. In the observed cases, there were no phishing emails, no exploitation of public-facing vulnerabilities, no malvertising and no compromised credentials.
Image Scanning with GitHub Actions
Scanning a container image for vulnerabilities or bad practices on your GitHub Actions using Sysdig Secure is a straightforward process. This article demonstrates a step-by-step example of how to do it. The following proof of content showcased how to leverage the sysdig-cli-scanner with GitHub Actions. Although possible, it is not officially supported by Sysdig, so we recommend checking the documentation to adapt these steps to your environment.
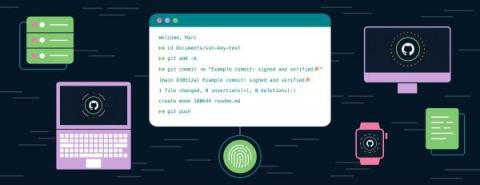
Sign your Git commits with 1Password
So 1Password CEO Jeff Shiner just committed code to one of my GitHub repositories. That’s strange. While he’s a developer at heart, I don’t think he gets much time to code these days. What’s going on here?
BlackHat 2022 key takeaways - Everything you need to know from BlackHat 25
Rediscovering argument injection when using VCS tools - git and mercurial
One of the main goals for this research was to explore how it is possible to execute arbitrary commands even when using a safe API that prevents command injection. The focus will be on Version Control System (VCS) tools like git and hg (mercurial), that, among some of their options, allow the execution of arbitrary commands (under some circumstances). The targets for this research are web applications and library projects (written in any programming language) that call these commands using a safe API.