Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Git
Malware analysis: Hands-On Shellbot malware
Malware analysis is a fundamental factor in the improvement of the incident detection and resolution systems of any company. The Sysdig Security Research team is going to cover how this Shellbot malware works and how to detect it. Shellbot malware is still widespread. We recorded numerous incidents despite this being a relatively old and known attack that is also available on open Github repositories.
How To Use Teleport: Using GitHub for Single Sign On (SSO)
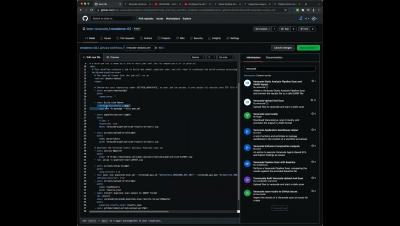
Anatomy of a Cloud Infrastructure Attack via a Pull Request
In April 2021, I discovered an attack vector that could allow a malicious Pull Request to a Github repository to gain access to our production environment. Open source companies like us, or anyone else who accepts external contributions, are especially vulnerable to this. For the eager, the attack works by pivoting from a Kubernetes worker pod to the node itself, and from there exfiltrating credentials from the CI/CD system.
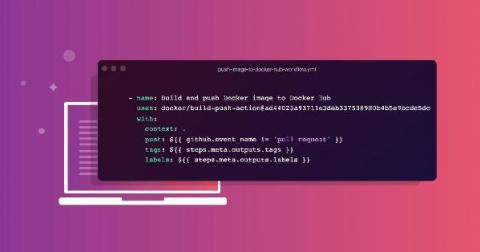
How to publish Node.js Docker images to Docker Hub registry using GitHub Actions
In a previous post, we presented a step-by-step tutorial on how to publish Node.js Docker images to GitHub Packages registry using GitHub Actions. In this post, we’ll focus on publishing the Docker image that we build to the public Docker Hub registry. Why is this useful you might ask? The Docker command line application docker has a default registry setting for docker.io which points to the Docker Hub registry.
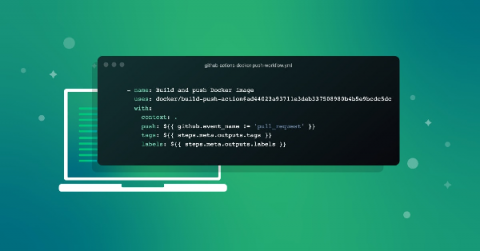
Managing Node.js Docker images in GitHub Packages using GitHub Actions
If you’re doing open source development today, chances are high that you’re active within the GitHub community — participating in open source projects and their repositories. A recent addition to the GitHub ecosystem is GitHub Packages, which was announced back in 2019 and is now receiving even more updates with the general availability of the GitHub Packages container registry.
EventSentry on GitHub: PowerShell module, templates and more!
Since we’ve accumulated a lot of resources around EventSentry that are updated frequently, we’ve decided to launch a GitHub page where anyone can access and download scripts, configuration templates, screen backgrounds and our brand-new PowerShell module that is still under development.
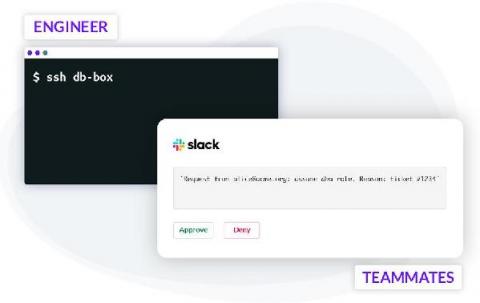
Pull Requests for Infrastructure Access
Making frequent changes to cloud applications running in production is the de-facto standard. To minimize errors, engineers use CI/CD automation, techniques like code reviews, green-blue deployments and others. Git pull requests often serve as a foundational component for triggering code reviews, Slack notifications, and subsequent automation such as testing and deployments. This automated process enforces peer reviews and creates enough visibility to minimize human error.
GitHub Security Code Scanning: Secure your open source dependencies
We are happy to announce Snyk Open Source support for GitHub Security Code Scanning, enabling you to automatically scan your open source dependencies for security vulnerabilities and license issues, as well as view results directly from within GitHub’s Security tab! A key ingredient of Snyk’s developer-first approach is integrating Snyk’s security data into the exact same processes that developers are using, whether this is within a developer’s IDE or a Git-based workflow.
Nightfall for GitHub, Now with Real-Time Data Loss Prevention
We are excited to announce that Nightfall DLP for GitHub now has two plans available: Pro and Enterprise. Both plans allow you to discover, classify and protect sensitive information in any GitHub organization by actively scanning your codebase for secrets, credentials, PII, and other business-critical data to notify you of data policy violations. The Enterprise plan provides the additional ability to scan the commit history of any repo within your GitHub org.