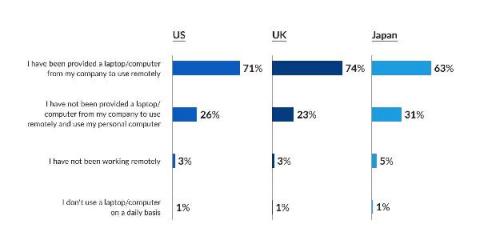
Everything You Need to Know About Neo Bank Security
Of all the modern business ecosystems, the Fintech sector is one of the most volatile landscapes that is teeming with industry and technological disruptions. And, adding to the pre-existing list is Neobanking. Currently, there are 246 neo banks in the world, and the market projections suggest an annual average growth rate (CAGR) of 47.7 percent until 2028, amounting to 722.6 billion U.S. dollars.