Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
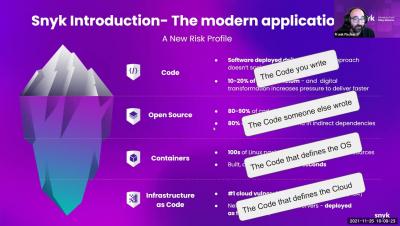
Snyk Code: An Introduction to Dev-First SAST
Blocking log4j with Response Actions - Sysdig Secure
The situation involving the log4j ( log4shell ) vulnerability has been rapidly evolving since its release a little over a week ago. A new exploit, CVE-2021-45046, was found which was not covered by the initial 2.15.0 patch. Not long after the 2.16.0 patch was released, another issue was found, CVE-2021-45105, which resulted in the release of 2.17.0. There is clearly a lot going on in the log4j library.
Log4j Incident Update - Dramatic Turn of Events
What Is Data Logging?
Humio is a CrowdStrike Company. Data logging is the process of capturing, storing and displaying one or more datasets to analyze activity, identify trends and help predict future events. Data logging can be completed manually, though most processes are automated through intelligent applications like artificial intelligence (AI), machine learning (ML) or robotic process automation (RPA).
Snyk Open Source in 2021: A year of innovation
More than 90% of organizations rely on open source software, a reliance that introduces a significant amount of security and legal risk via either direct or transitive open source dependencies. To overcome this challenge, Software Composition Analysis (SCA) solutions are playing an increasingly important role in helping organizations successfully identify and mitigate potential security issues.
Snyk Code in 2021: Redefining SAST
Starting in early 2021, Snyk Code and became available as a freemium offering for Snyk users. Snyk Code helps developers quickly and accurately find, prioritize, and fix security flaws in proprietary code. With detailed remediation guidance at every stage of the software development lifecycle (SDLC), from the developer’s environment (IDE) to continuous integration and development (CI/CD) pipelines, Snyk Code revolutionizes static application security testing (SAST).
How to evolve your organization into a data-centric security architecture
Defense strategies have evolved as hackers have changed their schemes, and one new approach companies are putting into practice for their security plan is data-centric security. Older security models focused on network infrastructure and hardware security controls while data-centric security concentrates on the data itself. This means data should be secure at all points regardless of where it is stored, processed, or where it is in transit.
How fully remote companies can create a culture of security from day one
In 2020, millions of businesses were thrust into remote work. What started as necessity has revealed lasting benefits for both employers and employees, though. The model improved productivity and employee morale, while lowering operational costs. Between these benefits and the continued priority of worker safety, many startups are launching with a remote or hybrid approach from the outset.