Threat hunting: Process, Methodologies, Tools and Tips
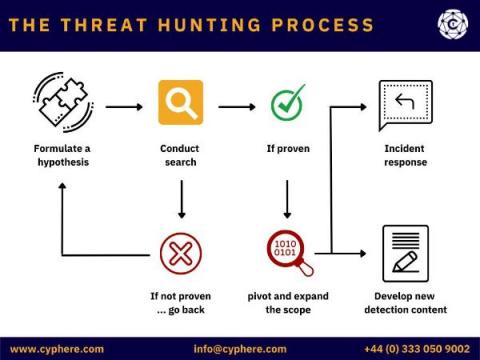
In cyber security, threat hunting is the act of proactively searching and monitoring networks, systems, endpoints, datasets etc. to identify any malicious behaviours or patterns that are not detected by existing security tools.