Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
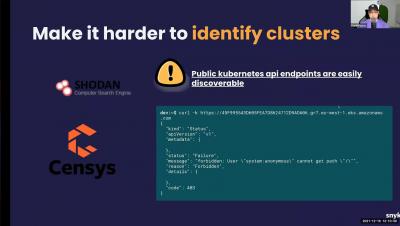
Cloud Security Posture Management
JavaScript type confusion: Bypassed input validation (and how to remediate)
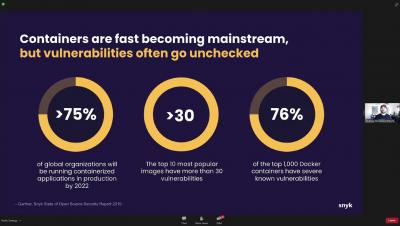
AWS Live Hack Workshop: Snyk and Docker
AWS Live Hack Workshop: Snyk and StackHawk
Third-Party Risk Management Framework: How to Select the Right One
Third-party technology providers can confer huge strategic advantages to a business. It allows each organization to focus on their highest value activities, but there’s a downside; new cyber security risks come with each partnership. Third-party risk is now an integral part of business ecosystems. A solid risk management framework is required to manage risk and keep you and your customers safe.
Top Cybersecurity Metrics (KPI) to Track
Cyber security KPI or other Key Performance Indicators are established in different areas of every organisation to track and monitor the progress towards attaining a certain goal or target. Cybersecurity is no exception here, and companies should maintain proper cybersecurity KPIs. There are many blog posts available around this topic but in this article, we have gathered a list of important cybersecurity KPIs that every organisation should consider.
Top 10 AT&T Cybersecurity blogs published in 2021
I enjoy being editor and managing this blog so much, I thought I'd share some of the best blogs of 2021. 2022 is right around the corner, but it's also a good time to look back at some 2021 highlights!
2022 and where Calligo is going
Our stated objective is simple: to be the world leader in data services. This is not easy. To be a world leader in anything requires notoriety, reliability, performance and ultimately, dominance. But we have a plan. As we close out 2021, there are certain things to look out for Calligo laying the groundwork for in 2022 …