Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
CISO's Corner: The Four Best Cybersecurity Investments You Can Make During the Cyber Talent Shortage
The need for strong cybersecurity has reached critical mass. Seventy-six percent of security leaders have reported an increase in cyber-attacks over the past year -- accelerated by the COVID-19 pandemic and a rapid shift from an in-office to a remote workforce and on-premises to cloud infrastructure.
Security Cloud Considerations for Delivering Security Service Edge (SSE)
In recent blogs, we’ve explored the role of Security Service Edge (SSE) technologies as part of a SASE architecture, and the key differences between SSE and SASE. But so far, we’ve focused more on overall functionality than on its realization and what SSE means from a cloud design and implementation perspective. In this post, we shift gears to put a spotlight on networking and infrastructure as it relates to security clouds.
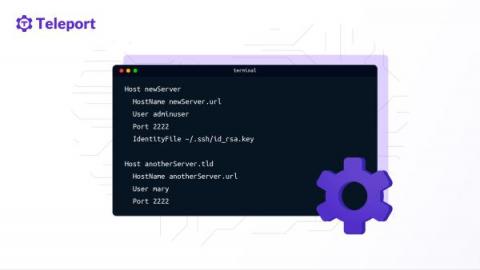
SSH Client Config Files and How to Use Them
SSH client configuration files allow us to connect to servers with pre-configured commands. This saves typing each SSH command parameter when logging into a remote machine and executing commands on a remote device. This article will examine secure shell (SSH) client configuration (config) files and their functions. Specifically, we will show an example of an SSH client config file to learn how to use these files before creating an example config file that connects to a fictitious server.
Behind the Buzzword: Four Ways to Assess Your Zero Trust Security Posture
With just about everything delivered from the cloud these days, employees can now collaborate and access what they need from anywhere and on any device. While this newfound flexibility has changed the way we think about productivity, it has also created new cybersecurity challenges for organizations. Historically, enterprise data was stored inside data centers and guarded by perimeter-based security tools.
Fourth Party Risk Management Explained
What You Should Know About the Rise in AWS S3 Security Data Breaches
The JNDI Strikes Back - Unauthenticated RCE in H2 Database Console
Very recently, the JFrog security research team has disclosed an issue in the H2 database console which was issued a critical CVE – CVE-2021-42392. This issue has the same root cause as the infamous Log4Shell vulnerability in Apache Log4j (JNDI remote class loading). H2 is a very popular open-source Java SQL database offering a lightweight in-memory solution that doesn’t require data to be stored on disk.
15 simple steps to stay secure at work without burning yourself out
No-one wants to feel burned out at work. Battling physical or emotional exhaustion can quickly impact your health, happiness, and any sense of professional fulfillment. That in turn can affect your productivity and the likelihood that you’ll make an honest mistake that puts your company’s data at risk.
AT&T teams with Cisco to create new managed SASE offering
Whether organizations call it digital transformation or just using technology to create opportunities for new, easier ways to work, one thing is certain. Businesses increasingly need to find simpler ways to securely build and manage new kinds of connections that support an era of: This is exactly the drive behind the latest collaboration between the cybersecurity and networking experts at AT&T and Cisco.