Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
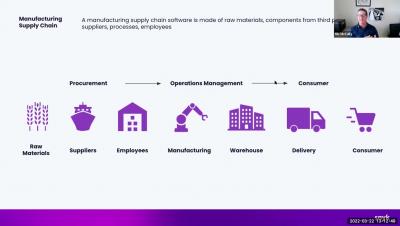
Ep 9 Securing the Digital Supply Chain - Punit Soni, Suki
Crowdstrike's Humio Platform Wins Data Technology Innovation Award for Log Analytics in 2022 Data Breakthrough Awards Program
The one-stop solution for keeping your IT environment secure
Cyberthreats continue to evolve, causing trillions of dollars in losses. There will be a 76% increase in cybersecurity breaches by 2024, according to StealthLabs. A report by IBM states that it took an average of 287 days to identify and contain a data breach in 2021. According to Verizon’s 2020 Data Breach Investigations Report, 86% of cybersecurity breaches were financially motivated, and 10% were motivated by espionage.
ManageEngine AD360 and Log360 bag the 2022 Cybersecurity Excellence Awards
ManageEngine kicks off the year on a high note as it bags the 2022 Cybersecurity Excellence Awards under various categories. To name a few, ManageEngine has been declared a winner for AD360’s IAM and identity governance (IGA) offerings, Log360’s SIEM and SOAR solutions, and data-centric security.
How to Mitigate Risks in Software Supply Chain Security
VPNs are increasingly common - how much can you see?
VPN tunnels are like shipping containers in that they are widely used (especially as the pandemic has moved more of the workforce to remote work), and they can be used to carry traffic for legitimate as well as malicious purposes. Establishing a tunnel between corporate offices, remote workers, or partners to transfer data is a legitimate and common use for VPNs.
A lasting trend: As a Service
With budgets tightening across the board and competition for a limited pool of IT and security talent growing fiercer, cyber as a service providers have become an optimal solution for many companies. Knowing they can count on their partners to focus on specific vectors, internal security teams can concentrate on their core missions. This could be high priority or critical items within security or something totally outside of security.
Helix Electric Takes Data Accessibility and Security to the Next Level
Vidar Malware Launcher Concealed in Help File
Appending a malicious file to an unsuspecting file format is one of the tricks our adversaries use to evade detection. Recently, we came across an interesting email campaign employing this technique to deliver the info stealer Vidar malware. First, let’s examine the email delivery mechanism, then go on to take a closer look at the Vidar malware itself. Figure 1: The malicious spam message The messages in this campaign have two things in common.