Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
How a Large Financial Services Firm Protects Against Data Leakage with Lookout Secure Email Gateway
Regardless of the industry or organization, corporate email is the main cause of unauthorized and accidental data leaks. Employees are constantly sending emails to external parties that may contain sensitive company data, personally identifiable information (PII), trade secrets and other intellectual property.
Containment, Communication, and Remediation: The 3 Keys to a Breach Response
The number of U.S. data breaches reported in 2021 increased dramatically over the preceding year. As reported by the Identity Theft Resource Center (ITRC), there were 1,291 data breaches between January 1, 2021 and September 30, 2021. The volume beat out the 1,108 breaches detected over the course of Full Year (FY) 2020. It’s therefore not surprising that data compromises year-to-date (YTD) was up 27% last year compared to FY 2020.
Top 5 Azure AD Security Best Practices
Azure Active Directory holds the keys to your Microsoft 365 kingdom. Responsible for vital functions such as authentication and authorization, Azure AD is ultimately responsible for managing access across the Microsoft cloud ecosystem. For that reason, is the target of many cyberattacks. In this blog post, we will detail the top 5 security best practices to follow to secure your Azure Active Directory and protect your business.
How To Detect & Mitigate Apache Log4j CVE-2021-44228
If you've already heard about the Apache Log4j CVE-2021-44228 (also known as Log4Shell and formally LogJam) vulnerability then you will know that this is a significant issue as many organisations are scrambling to secure their infrastructure from this critical remote code execution (RCE) vulnerability. With these considerations in mind, we wanted to bring you a guide that outlines the steps that can be followed to ensure the security of your systems from CVE-2021-44228.
Threat hunting: a top priority for businesses of all sizes
Today's threat actors are well-organized, highly skilled, motivated, and focused on their targets. These adversaries could be lurking on your network or threatening to break into it, using increasingly sophisticated methods to reach their goal. Simply put, there's often no need for adversaries to deploy malware at the early stages of the attack.
Mind Your Dependencies: Defending against malicious npm packages
Modern software projects are mostly composed of open source code. The question of who really controls this code, and is responsible for detecting and fixing software supply chain security issues, became a significant source of concern after the discovery of the Log4Shell vulnerability.
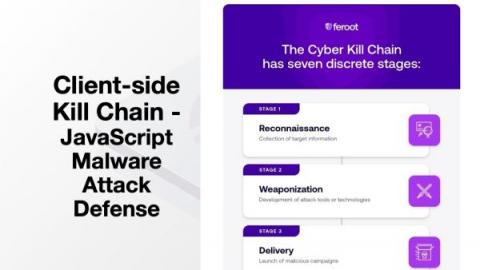
Client-Side Kill Chain: JavaScript Security Attack Defense
In my decade working in the cybersecurity industry, I’ve developed quite a few fond memories learning from talented security professionals. In 2015, I found myself working with Andy Pendergast at ThreatConnect. (As a little background, Andy is one of the fine folks who developed the Diamond Model for Intrusion Analysis. He is considered to be a veritable cybersecurity encyclopedia among his peers.) At the time, I was new to cyber threat intelligence (CTI).
15 Ways to Make SBOM Distribution Easy
The whole point of an SBOM is lost if you keep it a secret. Here we reveal our secrets of the ideal SBOM exchange. Let us know if we’ve missed anything in RKVST SBOM Hub. SBOMs are made for sharing and are the gifts that keep on giving, but only if they get to the right place at the right time to drive the right critical decision. The first critical decision, or moment of truth, is whether to buy a vendor’s product.
What Is Code Signing Certificate & What It Do?
It’s critical for software developers that users trust the software they’ve developed. Users have the full right to know that the software they’re downloading comes from a trusted source and not any malicious third party. And a code signing certificate helps you achieve that same trust.