Are vulnerability scores misleading you? Understanding CVSS severity and using them effectively
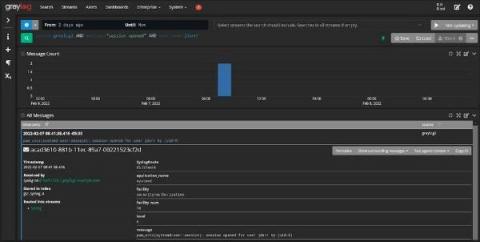
Vulnerabilities are everywhere. Vetting, mitigating, and remediating them at scale is exhausting for security practitioners. Let’s keep in mind that no organization has the capacity to find and fix all vulnerabilities. The key is to understand what a vulnerability is, interpret the meanings of the CVSS score, and prioritize and effectively use resources within constrained time limits or delivery windows. Since 2016, new vulnerabilities reported each year have nearly tripled.