Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
What XDR Isn't
STRT-TA03 CPE - Destructive Software
The Splunk Threat Research Team is monitoring several malicious payloads targeting Customer Premise Equipment (CPE) devices. These are defined as devices that are at customer (Commercial, Residential) premises and that provide connectivity and services to the internet backbone. Examples include.
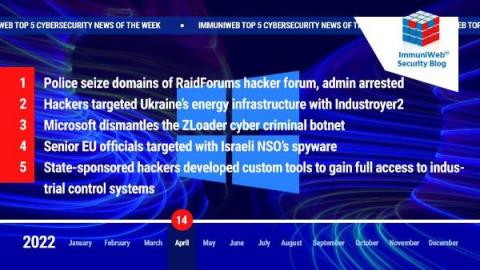
One of the World's Biggest Hacker Forums Dismantled in Global Law Enforcement Operation
Read also: Ukraine thwarts a Sandworm cyberattack against an energy provider, Microsoft disrupts the ZLoader botnet, and more.
How SecurityBridge & SECUDE offer additional layer of Data Security for SAP data
BlueHornet - One APT to Terrorize Them All
We Need a New Risk Management Approach to Secure Critical Infrastructure Against Russian Cyber Threats
A democratized approach to cybersecurity risk management that leverages continuous monitoring and public-private partnerships is overdue, and critical, for today’s cyber threat environment.
Customer Spotlight - Civo
For this customer spotlight we're highlighting Civo, a cloud-native service provider focused on Kubernetes. Bulletproof helps keep Civo's platform secure, giving peace of mind to their customers. In this edition we'll learn about Kubernetes and how it's rapidly becoming the de facto standard for managing cloud infrastructure to support modern applications. The COVID-19 pandemic has changed how we do business forever.
'Hackad' hacker: CISOs have more to worry about than a zero day exploit
When I look at IT security I can clearly see how it has changed, being today much more mature now than it’s ever been. Governments are working on policies and legislation forcing companies to prioritize IT security. As a result, the entire bug bounty community has bloomed in a way that I could never imagine, security researchers are now working together with companies to identify and mitigate vulnerabilities in a way that we have never done before.