Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Group Scope in Active Directory
IT pros are well aware that Active Directory has two types of groups: security groups, which are used to assign permissions to shared resources, and distribution groups, which are used to create email distribution lists. But not everyone understands that each of these Active Directory groups has a scope — and understanding how scope works is vital to security and business continuity. This blog post dives into what group scope is and exactly why it’s important.
3 Steps To Remain PCI Compliant with your AWS Configuration
Becoming and staying PCI compliant both take a lot of work. Developers are often already swamped with an endless list of tasks, and adding PCI compliance can be overwhelming. Security awareness is one thing, but a set of requirements is entirely different. It means you have less freedom in how you wish to implement security in your application, and you must understand the requirements demanded by your organization.
Alarming attacks on Internet of Medical Things (IoMT)
The impact of ransomware attacks on healthcare is as alarming as it is under-addressed. The United States healthcare system alone faces an annual burden of nearly $21 billion due to these attacks. It pays well over $100 million in ransoms, and is beginning to acknowledge the tragic realities of impacted patient care, including higher patient mortality rates. For every headline related to cyberattacks, there are likely hundreds more that go unreported.
Why IDcentral's AML Screening solution is dubbed End-to-End AML Compliance
The term Anti Money Laundering is abbreviated as AML. It is mostly used in the financial, legal, and compliance sectors to define the standard procedures that firms and organisations must implement in order to detect, identify, and report suspicious money laundering behaviour that may occur while carrying out their activity. AML compliance standards focus on anti-money laundering processes that deter and prohibit potential violators from participating in money laundering fraud or crime.
Integrity Monitoring Use Cases: Compliance
The IT ecosystems of enterprises are highly dynamic. Typically, organizations react to this volatility by investing in asset discovery and Security Configuration Management (SCM). These core controls enable businesses to compile an inventory of authorized devices and monitor the configurations of those assets. In addition to managing changes to their infrastructure, organizations must also keep an eye on the changes made to essential files.
An Introduction to the State and Local Cybersecurity Grant Program (SLCGP)
Cybersecurity funding in corporate environments has always been a source of anxiety for those who seek to keep organizations safe. When we examine the cybersecurity readiness of many state, local, and territorial governments, this funding struggle is taken to new heights of scarcity. Fortunately, a new program has been created by the Department of Homeland Security (DHS) to improve this shortfall, and better protect municipalities in the United States.
Things to Know about Sectigo Code Signing Certificate
Here is everything you need to know about Sectigo code signing certificates. Software security is one of the key concerns of businesses around the world. As the number of cyberattacks is increasing, it has become vital for businesses to ensure that their software is received graciously by the audience. This is where code signing steps in. Code signing is a process of signing the software code or driver with a digital signature using a code signing certificate.
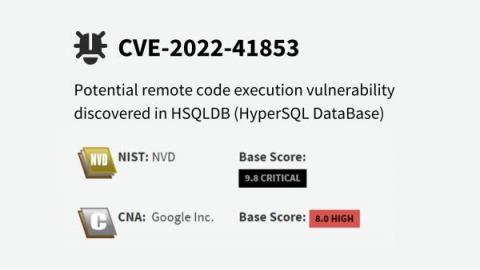
Remote Code Execution Vulnerability Discovered in HSQLDB
19.10.2022 - As part of our goal to continuously improve our vulnerability detectors, we continuously test various open-source projects with Jazzer within OSS-Fuzz. In this case, a test run yielded a severe finding with a potential remote code execution in a HSQLDB (CVE-2022-41853).
Detecting and mitigating CVE-2022-42889 a.k.a. Text4shell
A new critical vulnerability CVE-2022-42889 a.k.a Text4shell, similar to the old Spring4shell and log4shell, was originally reported by Alvaro Muñoz on the very popular Apache Commons Text library. The vulnerability is rated as a critical 9.8 severity and it is always a remote code execution (RCE) which would permit attackers to execute arbitrary code on the machine and compromise the entire host.