Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
What is Security Service Edge (SSE)
Cybersecurity Awareness Month: Recognize and Report Phishing
Securing your Cloud Infrastructure with Teleport and AWS IAM
Cloud security fundamentals part 3: Empower your developers
In our previous blog breaking down The 5 Fundamentals of Cloud Security, we looked at the value of prevention and secure design. Mapping resource relationships and enforcing security guardrails throughout development helps greatly reduce an available attack surface. But who will enforce these guardrails when your security team is busy with other work? This should be where developers are able to step in. So let’s look at another vital element in cloud security: empowering developers.
Clickbait: Think Before You Click
Meticulous Prep and Planning-A Linchpin of Modern AppSec Programs
This is the second of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles. It’s no exaggeration to say that IT and application security teams from all organizations are facing a perfect storm.
Shining a Light on Bots (From 'Phishy Business') | Cybersecurity Sessions bonus episode
How to Set Lock Screen Picture on Windows 10 Pro without Group Policy
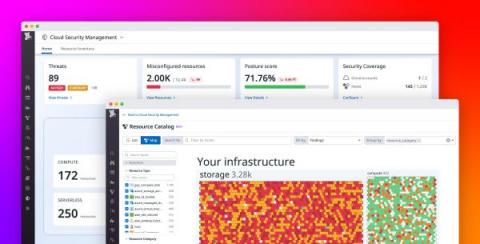
Add security context to observability data with Datadog Cloud Security Management
Organizations are rapidly migrating their infrastructure to the cloud, enabling them to modernize their applications and deliver more value to their customers. But this transition creates significant security risks that they may be unable to keep pace with. For example, cyber attacks on cloud resources are becoming more sophisticated and prevalent. Additionally, organizations often rely on legacy, disjointed security tools that don’t integrate well with cloud-native infrastructure.