Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Five Steps Towards Building a Better Data Security Strategy
In the past when organizations had a new security need, they would meet that need by purchasing a new security product. But that approach is how we ended up with an average of 76 security tools per enterprise, according to a 2021 survey from Panaseer. You may have a lot of tools, but that doesn’t mean your information is protected.
Phishing Scams Have Reached New Heights: How to Improve Detection and Response
The Anti-Phishing Working Group (APWG) Phishing Activity Trends Report reveals that in Q2 of 2022 there were 1,097,811 total phishing attacks. This marks the worst quarter for phishing observed to date, exceeding Q1 of 2022 which was the first time the three-month total exceeded one million.
Phishing: Taking a Multi-layered Defence Approach
What is Phishing? You have most likely heard the term phishing thrown around social media recently, and no, people haven’t taken up a new hobby at the local lake. The first known mention of the term “phishing” stems from a program named AOHell designed in the 1990s.
Introducing Styra Bundle Management Features
Adopting a fine-grained policy-as-code authorization approach based on Open Policy Agent (OPA)– the leading open-source policy engine– is a huge step forward in building microservices applications that run reliably and securely.
2022 Snyk Customer Value Study highlights: The impact of developer-first security
Developer-centric security movements have dominated discussions in software development over recent years. The concepts are clear — integrate security early and find issues faster. But how does an organization measure the success of its developer security program?
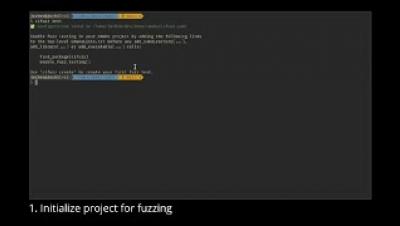
How to Set Up a Fuzz Test in Easy 6 Steps
Automate Keeper Device Approval in the Cloud with Azure
Keeper’s powerful Automator eliminates the repetitive task of device approval for Keeper administrators. With Keeper Automator, users will enjoy instant access to Keeper on any new device without having to wait for manual administrative approval. Now with Microsoft Azure support, administrators can deploy Keeper Automator to an Azure Container Service, providing a fully cloud hosted instance of Automator.
Cybersecurity Awareness Month: The Importance of Recognizing and Reporting Phishing Attempts
The theme of this year’s Cybersecurity Awareness Month theme – “See Yourself in Cyber” – focuses on how both individuals and organizations can better protect themselves from cybercrime. One of the most important steps we can all take is learning to recognize and report phishing attempts.
Infrastructure Security is Not Enough to Defend Against Ransomware
Register Now Let’s face it, you’re still vulnerable to ransomware. Even if it feels like you’ve done everything—you’ve built a robust defense, you have multiple cybersecurity measures in place, and you’ve implemented a company-wide security training. But, is it enough? Every business is vulnerable to ransomware. From the largest bank to the smallest school.