Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
A Swift Kick in the Nuts and Bolts of Banking
The global financial services industry is undergoing a seismic shift and not enough people are truly aware of what this means. By November of this year, banks and other financial institutions must have in place a new process for payment systems that uses the ISO 20022 standard instead of SWIFT. This must be active by November and by 2025, all financial institutions will have to be compliant.
Infrastructure as Code (IaC) - A Developer's Perspective
The organizations developed and deployed their IT infrastructure manually in the early days. The IT teams were responsible for the maintenance of hardware as well as software aspects of the infrastructure. Therefore, it is also applicable to the software development cycle. However, with technological advancement, many organizations have adopted cloud infrastructure for their business.
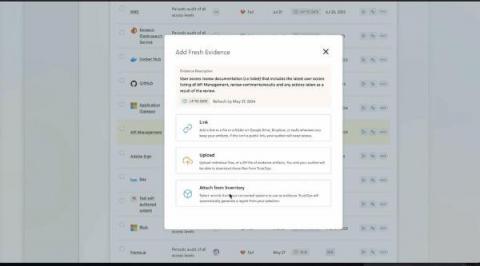
New In TrustOps: Evidence Automation with Smart Inventories
You want as much of your compliance program automated as possible, and collecting evidence to validate compliance controls always seems to take a lot of your team’s time. A considerable amount of control evidence involves providing accurate lists of artifacts to auditors — whether it’s workstations, tickets, alerts, or people. If only there were an easier way than having your teammates take screenshots and export lists from each of your internal systems.
The Nuvias Group Launches Nuvias ONE - the Digital Toolkit for Channel Partners
3 Steps to Secure and Compliant Data Sharing
Every day, organizations subject themselves to audit violations and data leaks when their end-users share sensitive data with third parties – essentially anyone outside of your organization. Various regulations and compliance frameworks require sensitive data to be encrypted with industry-grade security while at rest and in transit.
Goodbye passwords. Why Teleport is joining the FIDO Alliance
Passwords and other shared secrets are the number one cause of data breaches. The security risks of passwords is widely recognized in the consumer space with the leading tech companies (and competitors) including Microsoft, Google, Apple joining together to create the FIDO Alliance to reduce the over-reliance on passwords. With FIDO, passwords are replaced with more secure, and easier to use biometric and cryptographic authentication.
Exploit of Log4Shell Vulnerability Leads to Compromise of Major South American Vaccine Distributor
On June 23, The Cybersecurity and Infrastructure Security Agency (CISA) and the United States Coast Guard Cyber Command (CGCYBER) released a joint Cybersecurity Advisory (CSA) warning network defenders that cyber threat actors, including state-sponsored advanced persistent threat (APT) actors, have continued to exploit CVE-2021-44228 (Log4Shell) in VMware Horizon® and Unified Access Gateway (UAG) servers.
New MFA Bypass Phishing Method Uses WebView2 Applications with Hidden Keylogger
mr.d0x, a security researcher who previously released phishing tactics such as browser-in-the-browser (BitB) and utilized NoVNC to circumvent two-factor authentication (2FA), has released a new phishing attack method that exploits WebView2 applications to steal cookies and credentials. The code base utilizes a modified version of Microsoft’s WebView2 Samples repository. Microsoft has developed a new module called “Microsoft Edge WebView2 control”.
Malware on IBM Power Systems: What You Need to Know
Malware can come from and in a variety of attack vectors. Besides using ‘traditional’ methods of spreading malware, adversaries can leverage more sophisticated methods to turn your Power System into a ‘malware host’. The key target is your data. Data is valuable, and organisations have paid at least $602 million to ransomware gangs in 2021.