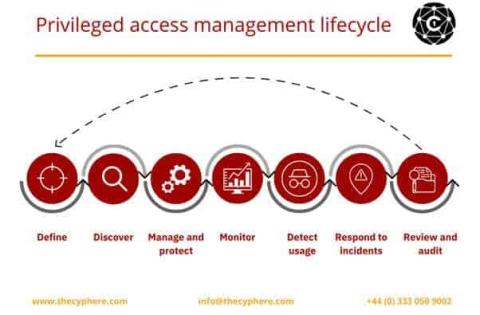
What is Privileged Access Management (PAM)?
Privileged account management is the process of identifying, controlling and monitoring privileged accounts and their associated activity. Privileged accounts are typically high-level administrator accounts that have broad access rights across an organisation’s IT systems. Because of their elevated level of access, these accounts pose a significant risk if they were to fall into the wrong hands.