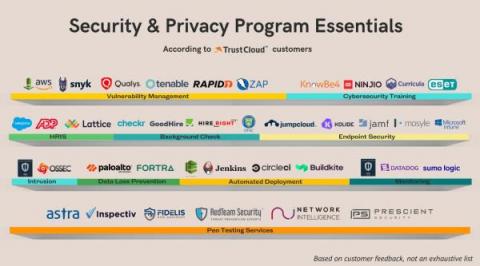
Your Shopping List for Security & Privacy Program Essentials
Whether your org is about to begin its journey for SOC 2, or you’re planning to wrangle up more standards (think ISO 27001, CMMC, and HIPAA, to name a few), the set of tools and software you have in place can be make-or-break. We asked our customers what their recommended tools were, and compiled your shopping list for security and privacy program essentials. Tools or services marked with * denotes a partner or integration.