Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Jazzer.js Brings Effective Fuzzing to JavaScript (Open-Source)
TL;DR Fuzzing JavaScript is easy now In this post, we introduce you to our new open-source fuzzer for the JavaScript ecosystem, Jazzer.js. Jazzer.js is a coverage-guided, in-process fuzzer for the Node.js platform. It’s based on the experience we gathered developing its namesake Jazzer, our fuzzer for the JVM platform. Internally, Jazzer.js uses libFuzzer as a solid industry-standard engine and brings many of its instrumentation-powered mutation features to JavaScript.
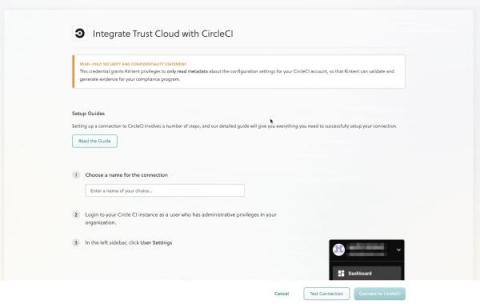
New Integrations Just Announced: CircleCI and Travis CI
Since working on a spreadsheet, you and your team have come a long way. You’re enjoying the ease of working in TrustOps because it automates control mapping, test creation, and evidence workflows. However, you’re looking for ways to save a bit more time, so you can focus on your day job and growing list of priorities. Collecting evidence to validate compliance controls takes time and affects your team’s productivity, including HR, IT, and DevOps.
Improving Information Security in the Age of Remote Work
Remote work has become popular among employees. 74% of workers say they would be less inclined to leave a company if they could work from home. No commuting, better work-life balance, greater flexibility, and increased motivation attract employees to telecommuting. Although companies offer remote work, data security concerns them. Employees might use unsecured wifi networks, leave their computers and laptops unattended, or carry confidential documents to public locations.
Torq Announces 385% Customer Growth and 360% Revenue Increase
Proven Ways to Slash Mobile App Security Costs
Mobile app security testing is expensive, and that’s a fact. For instance, a single quality penetration test costs around $20,000-$30,000. But do you essentially have to pay this high for the service? Mobile app development companies are cutting costs because of the economic meltdown or investors pulling out. And this could make it hard to set aside tens of thousands of dollars just for penetration testing, right? Moreover, without the right budget, how would you manage app security? Solution?
AT&T and Lookout expand partnership with launch of Lookout AlienApp
In order to secure data and protect against threats like ransomware, it’s critical to take a unified approach to endpoint security. To help security teams achieve this. Lookout and AT&T are expanding their partnership with the introduction of the Lookout AlienApp, which complements existing endpoint protection integrations in the USM Anywhere platform and helps to make the concept of true unified endpoint protection a reality.
Kubernetes version 1.25 - everything you should know
MasterCard allows Digital ID Verification of patients on Mobile Phones.
Seamless and smooth is the new mantra that every company is trying to achieve in their operation and client’s dealings. Healthcare services are adapting fast to this mantra, and the master card is the new revolution keeping the industry in sync with high user experience through the implementation of ID verification. It’s the digital age; almost everything in this world now operates with the help of AI and its different realms.
ReCAPTCHA 101: Is it the best way to block bots in 2022?
Bots now make up more than 43% of all internet traffic. It’s a growing problem — there are now almost twice as many bad bots as good bots. That’s why site administrators use programs like reCAPTCHA to block bots from accessing their websites, apps, and APIs. Bots aren’t a new problem. Back in 1950, Alan Turing created the Turing Test: a game designed to test a program’s ability to pass as a human.