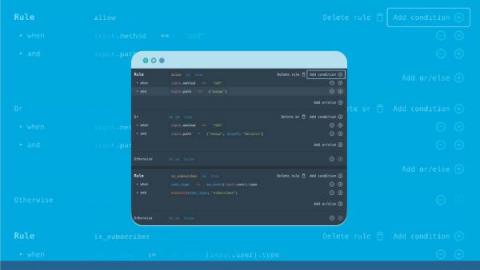
Oracle SBC: Multiple Security Vulnerabilities Leading to Unauthorized Access and Denial of Service
Oracle Communications Session Border Controller (SBC) is one of the most popular products worldwide that helps service providers deliver trusted, carrier-grade, real-time communications such as VoLTE, VoIP, video conferencing and calling, presence, IM, and IPTV. Harold Zang, Senior Technical Security Specialist and Jeremy Nunn, Security Specialist at Trustwave SpiderLabs, identified three vulnerabilities in the Oracle SBC.