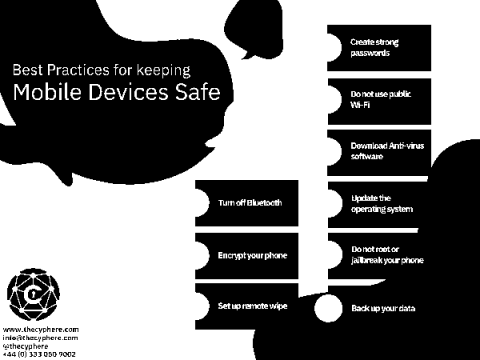
Mobile Device Security Guide: Securing your iOS and Android devices
There’s no doubt that mobile devices have become an integral part of our lives. We use them to stay connected with friends and family, get directions, check the news, and more. They’re always with us, convenient, versatile (texts, messages, calls, Internet, etc), keep us connected and loads another top reasons….in short, making our life easier! This is where mobile device security comes in, which helps protect your device from potential threats.