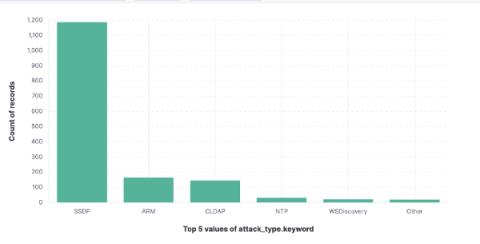
Compromised Credentials Postings on the Dark Web Increase 20% in Just One Year
Data trends show a clear upward momentum of posts from initial access brokers on the dark web, putting the spotlight on what may become cybersecurity’s greatest challenge. Any organization that has made cybersecurity a priority is laser focused on putting preventative measures, multiple means of detection, and a response plan in place.