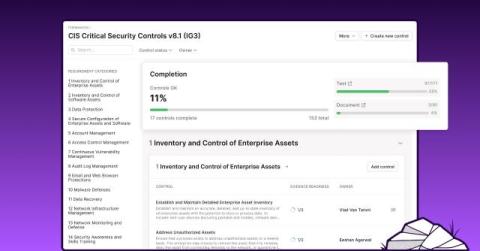
NIS 2 and EU Cybersecurity Act: Mandatory System Hardening
The NIS2 Directive is the European Union’s flagship cybersecurity law, poised to significantly strengthen cyber defenses across the EU when it takes effect on 17 October 2024. This upgraded version of the 2016 NIS Directive (NIS1) not only introduces stricter rules but also broadens its reach, covering more sectors and businesses, ensuring comprehensive protection and a stronger security posture.