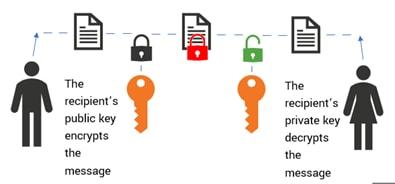
Adding security to Nuxt 3
Nuxt is an Intuitive Web Framework that allows you to build your next Vue.js application with confidence. It’s an open source framework under MIT license that makes web development simple and powerful. I highly recommend you check out the official website if you want to get started with it.