Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Vulnerability Assessment vs. Penetration Test: A Case of Mistaken Identities
If you’ve been in the realm of penetration (“pen”) testing in any capacity for any length of time, you’ve probably experienced the conversations around inconsistent pen testing results across teams or vendors. This isn’t anything new in the pen testing world. The conversations probably ranged from friendly internal team banter to more serious discussions with external vendors on pen testing program success metrics. Is this a case of mistaken identity?
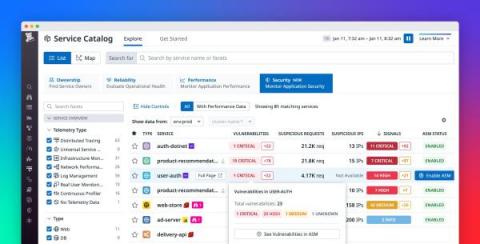
Gain visibility into risks, vulnerabilities, and attacks with APM Security View
As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.
What is vulnerability scanning?
Vulnerability scanning is the action of conducting an automated review of your system to look for potential risks and vulnerabilities. For budding information security professionals (or even those who have worked in the field for years), there is always something new to learn. Not only is it a highly intricate and advanced field but, on a daily basis, there is a cat-and-mouse game happening between security engineers and hackers.
CREST International give its support to the CyberUp Campaign
Cyber Threat Landscape Study 2023: Outpost24's honeypot findings from over 42 million attacks
What are the most common cybersecurity threats facing your business? The 2023 Cyber Threat Landscape Study provides valuable threat intelligence to help you implement the appropriate security measures against real threats. The Outpost24 research team is sharing the results of the attack data from a network of honeypots deployed to gather actionable threat intelligence. Here are the key findings from the 42 million attacks that were registered (between January 1 – September 30, 2022).
CVE-2022-47966: Researchers to Release PoC Exploit for Critical Vulnerability Affecting ManageEngine Products
Prevent OWASP Top 10 vulns with new Snyk Learn learning path
The holidays are over but the gifts keep coming! Introducing Snyk Learn learning paths! Our free developer-security education offering just got better! Snyk Learn provides free, high-quality education to developers created by security experts. We know it’s cold outside. We also know that we might be a little slow out the gate after the holidays. Emails? No more inbox 0. Slack messages? Too many to count.
The prevalence of RCE exploits and what you should know about RCEs
Recent headlines have indicated that some major companies were affected by Remote Code Execution (RCE) vulnerabilities, just in the month of October. RCE flaws are largely exploited in the wild, and organizations are continually releasing patches to mitigate the problem. RCE is a type of an Arbitrary Code Execution (ACE) attack where the threat actor executes malicious commands on the target’s device.
HIPAA Vulnerability Scan: Necessity, Requirements, And Steps
Healthcare statistics by HIPAA revealed that healthcare cybersecurity incidents fell by 8% in February 2022 but still faced 46 incidents affecting 2.5 million people.