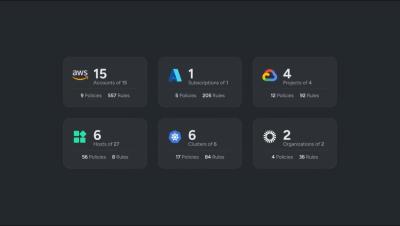
Improving AWS security services with Sysdig Secure
One of the primary goals of information security is to protect data, which of course entails protecting the resources that store and provide access to that data. According to the NIST Cybersecurity Framework, organizations need to develop and implement the necessary protections to restrict or mitigate the effect of a possible cybersecurity incident. Security should be integrated right from the source of the cloud architecture design process.