Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Dynamic Network Segmentation: A Must Have in the Age of Zero Trust
The top 3 data security problems plaguing tech companies
Tech companies building cloud-native applications face a set of unique and rising data protection challenges. At Bearer, we had the chance to speak with 100+ data security and privacy professionals including Chief Information Security Officers, Directors of Security Engineering, Application Security Engineers, Data Protection Officers, Privacy Engineers, and many more. Here are the top concerns that keep them up at night.
Snyk Open Source in 2021: A year of innovation
More than 90% of organizations rely on open source software, a reliance that introduces a significant amount of security and legal risk via either direct or transitive open source dependencies. To overcome this challenge, Software Composition Analysis (SCA) solutions are playing an increasingly important role in helping organizations successfully identify and mitigate potential security issues.
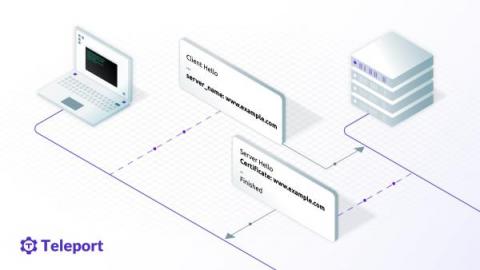
Leave SSL in the Dust, Turbocharge TLS with ALPN and SNI
As part of Teleport 8 we’ve made significant improvements to our routing, so much so the improvements have become a feature. Teleport 8 has new TLS routing that greatly reducing the port requirements needed for Teleport to run. Reducing the open network footprint down to a single port for your entire infrastructure and minimizing the attack surface. Want to know how we did it? Read on!
Security Service Edge (SSE) Considerations for the Future of Work
As we all learn how to practically apply the emerging technology of Secure Service Edge (SSE), here is a significant SSE use case—perhaps the most significant, at least in our immediate future. Looking ahead to 2022, many businesses will no doubt have return-to-office plans at the front of their minds. But coming back to the office brings its own unexpected risks that security leaders need to be ready for.
The Cloud Controls Matrix - what you need to know
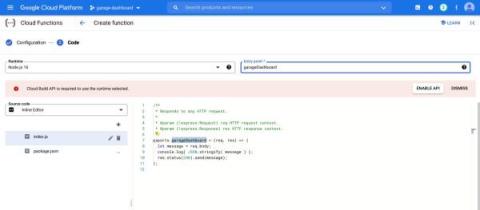
Cloud Function Dashboard with LimaCharlie
LimaCharlie provides everything you need to run modern cybersecurity operations, and it is also a great tool for builders. Our powerful web application is built using the publicly accessible API. There are no magic functions and we put the full power of the platform into the hands of those capable of wielding it. To demonstrate the kind of thing a user can easily build with LimaCharlie we have put together an interactive, embeddable dashboard.