Securing cloud workloads in 5 easy steps
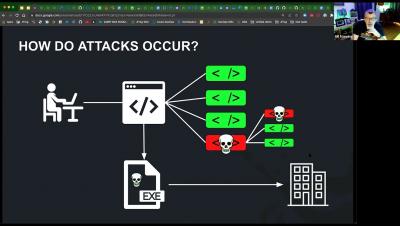
As organizations transition from monolithic services in traditional data centers to microservices architecture in a public cloud, security becomes a bottleneck and causes delays in achieving business goals. Traditional security paradigms based on perimeter-driven firewalls do not scale for communication between workloads within the cluster and 3rd-party APIs outside the cluster.