Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
In Cybersecurity, AI is Not A-OK
Artificial intelligence has been (and continues to be) a popular topic of discussion in areas ranging from science fiction to cybersecurity. But as much fun as it might be to discuss my favorite sci-fi AI stories, let’s set aside the works of Asimov, Bradbury and other storytellers to focus on the role of AI in cybersecurity.
How and why you should secure APIs
APIs are a crucial tool in today’s business environment. Allowing applications to interact and exchange data and services means that companies can provide an ever-greater range of features and functionalities to their clients quickly and easily. So, it is no wonder that a quarter of businesses report that APIs account for at least 10% of their total revenue - a number that will only increase in coming years.
What Is CSPM? A Closer Look at Cloud Security Posture Management
As we previously discussed in the Automating Your Cloud Security Posture Management (CSPM) Response blog post, CSPM is a vital component in any environment leveraging cloud services. Whether you are using a single cloud or are in a multi-cloud scenario, the complexity of these cloud platforms is constantly expanding. Staying on top of new changes in policies and functionality to ensure that you are maintaining a secure environment is daunting - and almost impossible to do without automation. No one has the resources to spend on maintaining a large team of cloud specialists who just audit everything that is in use.
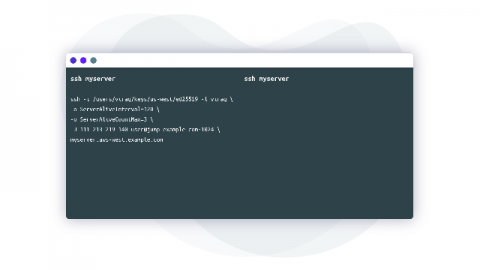
SSH configuration: ssh_config
This blog post covers some of my favorite settings for configuring the behavior of an ssh client (i.e. what is in the man pages for ssh_config). Whether you are looking to add some additional security constraints, minimize failures, or prevent carpal tunnel, ssh_config is an often underutilized, yet powerful tool. While the examples in this article focus on ssh configurations on unix based systems like linux and macOS, running an ssh server on windows is supported using openSSH.
Keeper One-Time Share for iOS
AWS Targeted by a Package Backfill Attack
On April 28 and April 30, respectively, WhiteSource Diffend identified, blocked, and reported two packages we deemed were malicious versions of original Amazon Web Services (AWS) packages. Whitesource security experts have reached out to contacts at Amazon to notify them of our findings. This discovery may point to a new takeover method that targets packages of well-known origins, in this case, AWS.
Choosing Open Source Libraries
CrowdStrike Delivers Adversary-Focused, Platform Approach to CNAPP and Cloud Security
Cloud-based services have revolutionized business processes and emerged as the backbone of the modern enterprise. According to analyst firm Gartner®, “more than 85% of organizations will embrace a cloud-first principle by 2025 and will not be able to fully execute on their digital strategies without the use of cloud-native architectures and technologies.”
Rethinking Privileged Access Management for Cloud and Cloud-Native Environments
SSH was designed in 1995, LDAP was initially developed in 1993, and role-based access control was introduced in 1992. The concept of least privilege was introduced in 1975. With all of these existing technologies, when are modern privileged access management solutions necessary? This is a common question asked when we pitch the idea of modern privileged access management (PAM).