Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
2 - How Zaraz Works
3 - Introduction to Cloudflare
ChatGPT's Role in the Evolution of Application Development
When I wrote my first applications in high school, coding was a lot more time-consuming. I didn’t have libraries I could shop through with ready-made bits of code to drop in to save myself time or bridge the gap between the pieces of code I could write to create something more complex. Instead, I had to write everything from scratch. If I wanted to include any kind of image, I would have to draw it with mathematical coordinates, which took a ton of time.
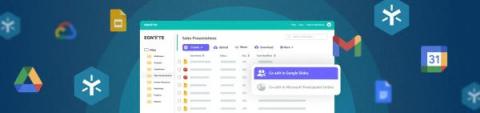
Real-time co-editing on desktop using native Google Workspace tools
With deep integrations into Google Workspace, Egnyte enables users to streamline the document creation process by delivering a seamless experience to create, co-edit and share documents directly from within the Egnyte Desktop App and Web UI. By using Egnyte as the document source, files are also protected from internal misuse and external threats, ensuring that users can collaborate with confidence, without concerns of exposing sensitive data.
Mapping the MITRE ATT&CK Framework to API Security
What is Certificate Management? Definitions and Benefits to Securing the IoT
In today’s digital age, online security has become a major concern for businesses of all sizes. With the increasing number of cyber-attacks and data breaches, it is crucial that organizations take measures to protect their sensitive information from falling into the wrong hands. This is where SSL/TLS certificates come in handy as they provide encryption and authentication to ensure secure communication between servers and clients.
AI, ChatGPT and Identity Security's Critical Human Element
In 1999, a far-fetched movie about a dystopia run by intelligent machines captured our imaginations (and to this day, remains my favorite film). Twenty-four years later, the line between fact and fiction has all but vanished and the blockbuster hits much differently. Are we entering the Matrix? Are we already in it? Can anyone be sure?
SaaS-based IoT Security Solutions
The advent of connected devices has brought about significant change in the technology industry. We all accept that data is power – the more we know about our devices and users, the more effectively we can serve their needs. The integration of connected devices has transformed several industries, including healthcare, transportation, and manufacturing.
What Is IoT Device Management? Definition, Key Features and Benefits
IoT Device Management (IDM) is a software platform that helps businesses manage their IoT devices, from identifying and tracking assets to automating operations. IDM features a wide range of features to help businesses manage their IoT devices. IoT device management platforms allow you to remotely control, monitor and update your entire fleet of IoT devices at scale.