Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
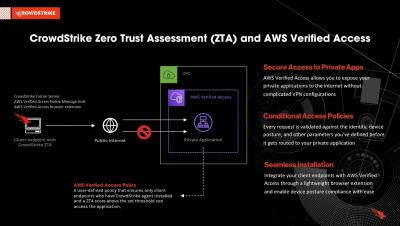
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
AWS Verified Access (AVA), a feature of Amazon Virtual Private Cloud (VPC) networking, delivers secure, zero-trust access to private applications without a VPN by continuously evaluating each request in real time based on contextual security signals like identity, device security status and location. The service grants access based on the security policy configured for each application and then connects the users, thereby improving the security posture of the organization.
The 443 Podcast, Ep. 236 - Another Software Supply Chain Attack
Hands-on guide: How to scan and block container images to mitigate SBOM attacks
According to OpenLogic’s Open Source Adoption and Expansion in 2022 Report, the adoption of Open Source Software (OSS) across all sizes of organizations is rising with 40% of respondents stating an increase of OSS software over the previous year and 36% reporting a significant increase in OSS software usage. The increase in OSS adoption can be attributed to a number of factors including access to the latest innovations, reduction in costs and frequent product updates.
Mend.io Achieves AWS Security Competency Status
We’re delighted to announce that Mend.io has achieved Amazon Web Services (AWS) Security Competency status. This designation recognizes that Mend.io has demonstrated proven technology and deep expertise to help customers achieve cloud security goals. It reinforces Mend.io’s position as a trusted member of the AWS Partner Network (APN), which has already been established since we achieved AWS DevOps Competency status.
Securing private applications with CrowdStrike and AWS Verified Access
Deceptive 'Vibranced' npm Package Discovered Masquerading as Popular 'Colors' Package
A new malicious package has been detected on the Node Package Manager (npm) repository that poses a significant threat to users who may unknowingly install it. Named ‘Vibranced,’ the package has been carefully crafted to mimic the popular ‘colors’ package, which has over 20 million weekly downloads.
[Head Start] Effective Methods How To Teach Social Engineering To An AI
Remember The Sims? Well Stanford created a small virtual world with 25 ChatGPT-powered "people". The simulation ran for 2 days and showed that AI-powered bots can interact in a very human-like way. They planned a party, coordinated the event, and attended the party within the sim. A summary of it can be found on the Cornell University website. That page also has a download link for a PDF of the entire paper (via Reddit).
Cloud Identity Security: It Doesn't Taste Like Chicken
There’s a scene in the original “Matrix” movie when Neo is sitting in the grimy kitchen with the rest of the crew and eating gray, runny slop. No matter what new version of gray slop they eat, they always seem to think that it tastes like chicken. When confronted with something new, it’s a natural human trait to relate it back to something we already know.
Effective AWS Incident Response: Examples and Recommendations
The use of Amazon Web Services (AWS) in organizations around the world is prolific. The platform accounted for 31% of total cloud infrastructure services spend in Q2 2022, growing by 33% annually. Despite its widespread use, many organizations still fail to consider the nuances of incident response in AWS.