Win The AI Wars To Enhance Security And Decrease Cyber Risk
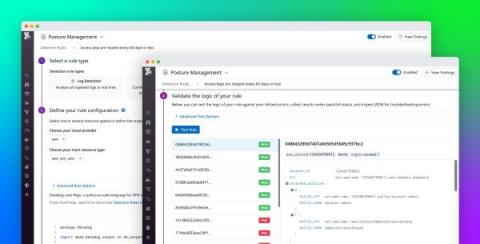
With all the overwrought hype with ChatGPT and AI…much of it earned…you could be forgiven for thinking that only the bad actors are going to be using these advanced technologies and the rest of us are at their mercy. But this is not an asymmetric battle where the bad actors use AI and the rest of us are struggling using our pencils and abacuses to catch up. It is the good side that invented and is accelerating AI. It is the good scientists that made ChatGPT and all of its competitors.