Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Securing Your Software Supply Chain with JFrog and Azure
Power of AI in Protest Planning | Ensuring Safety and Security
The Basics of Cloud Security Glossary
What is it: Agentless architecture refers to platforms and services that are built to run as cloud-native applications. They require no installation, patching, or other forms of long term upkeep on the part of a user. Why it matters: Agentless applications, especially agentless security applications have a lower total cost of ownership (TCO), in terms of man-hours saved in deployment, maintenance, and overhead.
Enterprise Users Sending Sensitive Data to ChatGPT
ChatGPT use is increasing exponentially among enterprise users, who are using it to help with the writing process, to explore new topics, and to write code. But, users need to be careful about what information they submit to ChatGPT, because ChatGPT does not guarantee data security or confidentiality. Users should avoid submitting any sensitive information, including proprietary source code, passwords and keys, intellectual property, or regulated data.
Transforming defence with Elastic AI and data capabilities
Spectrum of Mobile Risk- Lookout
Research with Snyk and Redhunt Labs: Scanning the top 1000 orgs on GitHub
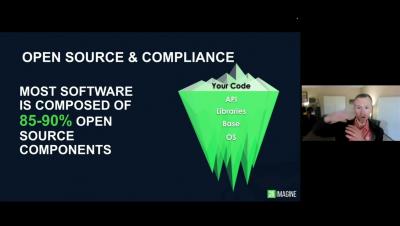
Open source code is a vital aspect of modern development. It allows developers to increase their application’s functionality, while reducing overall development time. However, the system isn’t perfect. The nature of third party software and it’s dependencies often creates opportunity for security vulnerabilities to lurk in libraries and downloads.