Web Design Best Practices for Multichannel Content Management
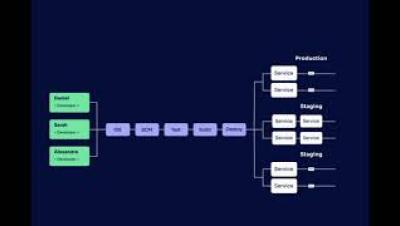
In today's digital landscape, understanding multichannel content management is crucial for web design businesses aiming to maximise their reach and impact. A robust multichannel strategy involves managing and distributing content across various platforms, ensuring consistent and cohesive communication with the audience.