|
By Jit
We’re thrilled to announce that Jit has achieved the AWS Security Competency, a significant milestone that underscores our commitment to revolutionizing product security for developers and security teams alike. This recognition from AWS validates our leadership in the security space and highlights the value we bring to organizations looking to embed automated security into their development workflows.
|
By Jit
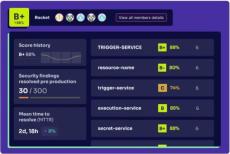
Application Security Posture Management (ASPM) emerged to address gaps in traditional application and cloud security scanners – like SAST, SCA, secrets detection, IaC scanning, CSPM, and many others – that generate noisy alerts and silo security insights across various tools. By providing a consolidated view of product security risks that are prioritized according to their business and runtime context, ASPM helps security teams understand which issues truly matter.
|
By Jit
Product security leaders face the monumental task of identifying and safeguarding their most critical cloud and application assets within large and complex cloud environments.
|
By Jit
Securing applications is more challenging than ever. Companies are faced with increasingly complex infrastructures that demand higher levels of protection to mitigate security risks effectively. That’s why Jit is thrilled to announce our new partnership with Loom Security, a leading professional services firm dedicated to helping companies secure their applications in the cloud.
|
By David Melamed
Today, we’re thrilled to announce Jit’s certified integration with Wiz! This partnership will make it easier than ever for developers to consistently resolve security issues before production, and for security teams to unify and prioritize the top risks in production – effectively bridging the gap between the core objectives of ASPM and CNAPP. We believe that securing apps in the cloud has been overcomplicated by tool sprawl, alerting noise, and a disjointed UX for developers.
|
By Jit
When it comes to securing applications in the cloud, the challenge isn’t detecting potential security issues. There are hundreds of application security tools and cloud security tools that are capable of surfacing code flaws and security misconfigurations that could lead to vulnerabilities. The real challenge is empowering development teams to adopt these tools to consistently improve the security posture of their services.
|
By Charlie Klein
While code and cloud security scanners are great at identifying code flaws and cloud misconfigurations, they can bombard developers with long lists of potential security “issues” – many of which don’t introduce real risk. Whether insecure code introduces real risk depends on a number of factors, like whether it is being deployed to production, is exposed to the internet, or calls a sensitive database.
|
By David Melamed
Today, I’m thrilled to announce Jit’s full support for GitLab, which will significantly expand our ability to execute our mission to empower every developer to secure everything they code. This new integration will provide all of the same benefits that we’ve been delivering to our customers on GitHub for years, including: If you’re on GitLab, check out the guidelines below to quickly realize these benefits.
|
By Ohav Almog
AWS-Vault is an excellent open-source tool by 99Designs that enables developers to store AWS credentials in their machine keystore securely. After using it for a while at Jit, I decided to dig deeper into how it works and learned a lot along the way. In this article, I will summarize and simplify the information I learned to help others with their aws-vault adoption and lower the barrier to usage.
|
By Ohav Almog
In programming, the term idempotence may sound like a complex and arcane concept reserved for mathematical discussions or computer science lectures. However, its relevance stretches far beyond academia. Idempotence, also called idempotency, is a fundamental principle that is pivotal in ensuring software systems’ predictability, reliability, and consistency.
|
By Jit
Learn how Jit Teams provides a dedicated security portal for every development team, so they can have full visibility into the security of their services and understand where to focus remediation efforts.
|
By Jit
In five minutes, explore Jit's core product capabilities to empower developers to secure everything they code and unify product security risk mitigation.
|
By Jit
Amir Kessler provides his perspective on prioritizing vulnerabilities based on their runtime and business context.
|
By Jit
Chris provides his perspective on Jit's approach to unifying leading open source product security scanners in one place to consolidate scanning, prioritization, and remediation.
|
By Jit
Amir Kessler gives his perspective on one of the fundamental challenges of AppSec – making sense of huge volumes of product security issues – and how ASPM can solve this problem.
|
By Jit
Chris Hughes describes the advantages of product security orchestration, which enables security teams to plug their favorite scanners into a single framework that unifies the execution and UX of multiple tools.
|
By Jit
Learn how to integrate Jit with GitHub to start scanning your codebase for security vulnerabilities, while implementing continuous scanning for newly introduced vulnerabilities.
|
By Jit
Learn how Clasp unified static analysis, open source license checking, DAST, IaC scanning, and more with Jit.
|
By Jit
Learn how Clasp was able to quickly set up Dynamic Application Security Testing (DAST) to scan their web apps for vulnerabilities on a schedule.
|
By Jit
Learn how Clasp's developers use Jit to consistently resolve code security vulnerabilities before production.
- November 2024 (10)
- October 2024 (6)
- September 2024 (3)
- July 2024 (3)
- June 2024 (8)
- May 2024 (13)
- April 2024 (21)
- March 2024 (11)
- February 2024 (9)
- October 2023 (3)
- September 2023 (3)
- August 2023 (1)
- June 2023 (3)
- May 2023 (2)
- March 2023 (1)
- February 2023 (2)
Jit is the easiest way to secure your code and cloud, providing full application and cloud security coverage in minutes. Tailor a developer security toolchain to your use case and implement it across your repos in a few clicks.
Jit empowers developers to own the security of their code without ever leaving their workflow, prioritizing the alerts that matter. Using your current security toolset with Jit, your devs can deliver secure code faster than ever.
Full Security Coverage in Minutes:
- Iterative scanning within the PR makes Jit easy to adopt for developers: Fast and automated scanning within GitHub make security checks feel like quality checks, so developers can easily incorporate Jit into their day-to-day.
- Gamified security tracking per team: Every team can monitor their security score, which is based on open vulnerabilities in their repos.
- Leverage an open and extensible orchestration framework: Easily plug any tool into Jit’s extensible orchestration framework to unify the execution and interface of any security tool, enabling a more consistent DevSecOps experience.
The easiest way to secure your code and cloud.