Keeping Financial Services Organizations Secure in an AI World
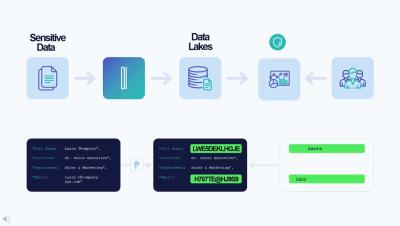
When we talk about financial services and technology, security and regulatory compliance are always top of mind. And now, Generative AI has entered the chat - one of the most talked-about technologies of recent years. And Financial Services institutions have only begun to scratch the surface of what generative AI can do. The problem is, so have cyber threat actors. In this session from Splunk, and IDC, you’ll hear key insights into how financial services companies are improving their security posture in an AI World, and how those practices can benefit your organizations.