|
By Anirban Banerjee
India's Digital Personal Data Protection (DPDP) law, enacted in 2023, represents a pivotal step in safeguarding personal data privacy while fostering accountability among entities handling such data. As businesses grapple with its requirements, understanding its core mandates, applicability, timeline, and implications is critical for compliance and operational efficiency.
|
By Anirban Banerjee
LLMs are based on neural network architectures, with transformers being the dominant framework. Introduced in 2017, transformers use mechanisms called attention mechanisms to understand the relationships between words or tokens in text, making them highly effective at understanding and generating coherent language. Practical Example: GPT (Generative Pre-trained Transformer) models like GPT-4 are structured with billions of parameters that determine how the model processes and generates language.
|
By Anirban Banerjee
Cyber insurance underwriters consider a range of variables to assess the risk a company presents and, consequently, determine premiums. These variables can broadly be categorized into organizational factors, security posture, third-party interactions, and incident history.
|
By Jackson Harrower
This collaboration is a significant step forward in making robust data security accessible to all organizations. By leveraging the Azure Marketplace, we're empowering Azure customers to easily discover, deploy, and integrate Riscosity into their existing infrastructure. This seamless integration allows for a streamlined experience and faster time to value.
|
By Anirban Banerjee
While Data Security Posture Management (DSPM) is a powerful approach for discovering, monitoring, and managing sensitive data across complex systems, it is not without its challenges. These hurdles often stem from the complexity of modern data environments, evolving threats, and operational constraints. Below are the primary challenges associated with DSPM.
|
By Anirban Banerjee
The General Data Protection Regulation (GDPR) of the European Union and the California Privacy Rights Act (CPRA) represent landmark regulations designed to protect consumer data privacy. While GDPR became enforceable in May 2018, CPRA came into effect in January 2023, building on its predecessor, the California Consumer Privacy Act (CCPA). Both laws aim to empower individuals with greater control over their personal data while imposing rigorous obligations on businesses.
|
By Anirban Banerjee
In an era where data breaches, privacy violations, and regulatory fines dominate headlines, the need for robust privacy engineering has never been more critical. Yet, despite its growing prominence, privacy engineering is failing to meet the demands of businesses and consumers alike. To understand why, let’s explore what privacy engineering is, the challenges it faces, why its current state is insufficient, and the transformative shift needed to make it truly effective.
|
By Anirban Banerjee
In today’s business ecosystem, data exchanges are critical for operations. From APIs to FTP connections, Electronic Data Interchange (EDI), and Virtual Desktop Infrastructure (VDI), data transfers happen continually, each using specific protocols and requiring authentication to ensure security and confidentiality. These interactions rely on a vast array of identities, keys, and credentials that need consistent management and periodic rotation to maintain security.
|
By Anirban Banerjee
The Okta 52-character username vulnerability has brought to light a significant security issue within the popular identity and access management (IAM) platform used by many enterprises worldwide. This vulnerability allows attackers to exploit a username constraint to bypass certain authentication checks, which could have severe implications for businesses relying on Okta’s services for secure user verification and access control.
|
By Anirban Banerjee
API calls are the backbone of modern software, enabling applications to communicate and share data seamlessly. However, with this integration comes the challenge of understanding and managing the identities used in API calls. These identities, often tied to authentication and authorization mechanisms, are crucial for determining what data is accessed and exchanged.
|
By Riscosity
Welcome to the third installment of Riscosity’s Lightning Interview Series In this episode, we sit down with Barak Engel, founder and CEO at EAmmune, and CISO at MuleSoft, Amplitude, StubHub, BetterUp, and Faire among others. Barak is also the author of Why CISOs Fail, The Security Hippie, and The Crack in the Crystal. Ever wonder how you pentest a novel? Tune in to find out.
|
By Riscosity
Welcome to the second installment of Riscosity’s Lightning Interview Series In this episode, we sit down with Michael Machado, a security industry veteran and former CISO at public and pre-IPO companies including RingCentral, Shippo, and BeyondTrust. Ever wonder the best strategy for gaining meaningful budget increases as a CISO? Tune in to find out.
|
By Riscosity
Welcome to the first installment of Riscosity’s Lightning Interview Series. We'll be sitting down with industry leaders for informative and to-the-point conversations. In this episode, we chat about the present and future of internal audit and data security with Nauzer Gotla, Vice President of Internal Audit at Nextracker (NASDAQ:NXT), a dominant player in solar tracking solutions with revenues north of $2.5B.
|
By Riscosity
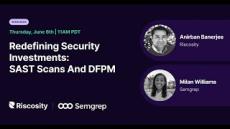
In today's ever-evolving digital landscape, teams must have a strong understanding of the security measures that will work best for their environment and how to implement them. During this event, we explore the benefits of utilizing SAST scans and DFPM (Data Flow Posture Management) tools to create robust security guardrails for your organization. Hear from Anirban Banerjee, CEO and Co-founder of Riscosity, and Milan Williams, Sr. Product Manager at Semgrep, as they dive into how teams can approach security investments starting with SAST scans and data flow security.
|
By Riscosity
A wonderful conversation with two amazing security leaders! We talk about compliance, security programs, API security, Software supply chain, strategies - and oh so much more. A true treat for security lovers.
|
By Riscosity
In this video we talk with two security leaders, very well known, from the Bay Area - Mike Hamilton and Barak Engel. A variety of topics, including software supply chain, data governance and APIs amongst many are discussed.
|
By Riscosity
An amazing conversation with Peeyush Ranjan, Engineering VP at a Fortune 50 organization. Peeyush coined an amazing term - "Diffused Responsibility" - this is the reason why we all, in different silos, development, security, GRC, legal have to try harder and pull towards the same goal. In fact the example used - of a sports team, getting the pigskin over the line is a very apt one.
|
By Riscosity
We chat about the Health-tech space. What are the challenges of building a Healthtech company, where are the roadblocks, what should you look out for - very introspective feedback from Punit! A must hear for entrepreneurs..
|
By Riscosity
In this episode of Securing the Digital Supply Chain we talk with terence Jackson, CISO at Microsoft for State and Local Government customers! We have a great time talking about the trends in the Software Supply Chain area as well what can CISOs focus on to get quick wins for their organizations. Terence brings a wealth of experience from small to medium scale to large enterprise organizations and applies them to various security challenges to effectively solve them.
|
By Riscosity
Yaser is a veteran in the construction industry and in this session we learn about what technologies are used in the construction technology sector, what are some of the gotchas that industry leaders should pay attention to and the various types of organizations that are there on the landscape..
- December 2024 (6)
- November 2024 (9)
- October 2024 (7)
- September 2024 (2)
- August 2024 (5)
- July 2024 (1)
- June 2024 (2)
- May 2024 (1)
- April 2024 (2)
- March 2024 (3)
- February 2024 (3)
- January 2024 (3)
- December 2023 (4)
- November 2023 (4)
- October 2023 (2)
- August 2023 (1)
- June 2023 (3)
- March 2023 (1)
- January 2023 (1)
- October 2022 (3)
- April 2022 (1)
- March 2022 (1)
- February 2022 (5)
- January 2022 (5)
- November 2021 (1)
Riscosity enables full control, visibility, and compliance for data going to third parties and AI tools. Deployed on-prem and in your private cloud.
Riscosity is the data flow security platform that empowers teams to have full visibility of third party data in transit and automate the redaction or redirection of sensitive data simplifying how companies meet security and privacy standards.
How it works:
- Monitor: Track and pinpoint any data being sent to a third party API.
- Track: Easily map data sub processors and the information shared with them.
- Remediate: Automatically replace detected sensitive data with redacted inputs.
- Comply: Continuously monitor and block APIs from sending the wrong data to the wrong place.
Deploy Riscosity in your production or development environment to monitor, identify, redact, and secure all third party APIs.