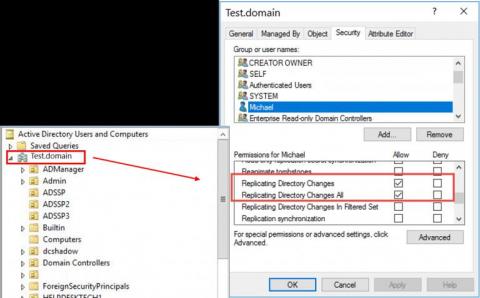
The Second Critical Step to Building the Modern SOC
The new Devo eBook, Building the Modern SOC, presents four evolutionary steps for creating a highly automated and efficient security operations center (SOC) that empowers analysts. This is the second in a series of posts about the four steps that highlight some of the most important concepts. The first post covered Step 1, which is about establishing a foundation of centralized, scalable visibility. This post excerpts Step 2, extracting intelligent insights from your data.