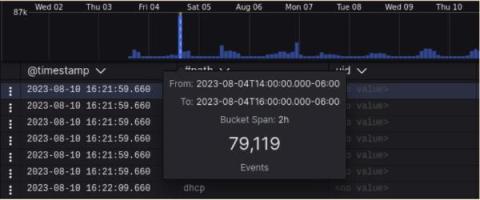
How Long Before Governments Ban Use of Security Appliances?
Enterprises in the private sector look to the US federal government for cybersecurity best practices. The US CISA (Cybersecurity & Infrastructure Security Agency) issues orders and directives to patch existing products or avoid use of others. The US NIST (National Institute of Standards and Technology) publishes important documents providing detailed guidance on various security topics such as its Cybersecurity Framework (CSF).