Navigating Network Security: A Structured Approach to Security Testing
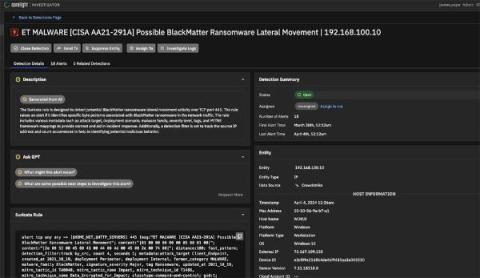
Companies must prioritise a comprehensive and proactive approach to network security. Among the most effective strategies to ensure robust defence mechanisms is rigorous penetration testing. By adopting an “assumed breach” mentality, organisations can better prepare for potential attacks, ensuring they are not merely reacting to threats but actively preventing them.