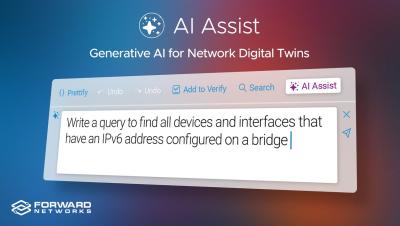
Sumo Logic Cloud SIEM explainer video
Sumo Logic Cloud SIEM helps teams broaden threat visibility across the entire enterprise. With uniformity, clarity and transparency, companies can bring all their security tools together for complete visibility. Cloud SIEM automates real-time threat investigation, incident management and threat response while reducing false positives and analyst fatigue. Bring your teams together with centralized data and cloud-native scale in a SaaS Log Analytics Platform that breaks down silos.