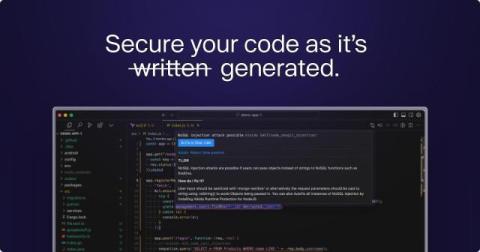
How Can You Identify Your Internet-Facing Applications?
In today's digital landscape, organizations are increasingly reliant on internet-facing applications to conduct business and engage with customers. However, many organizations are unaware of the full extent of their internet exposure. Can you secure your organization if you do not know which internet-facing applications you own? Not effectively.