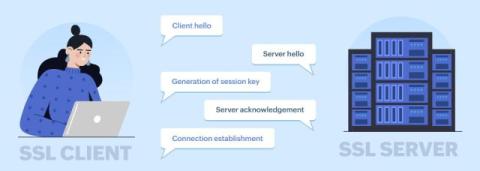
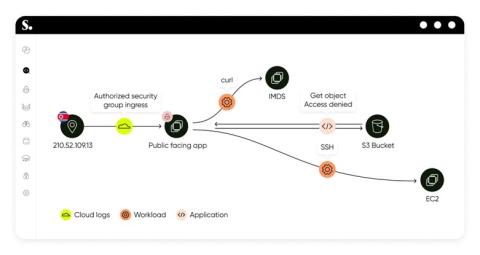
Grow Your MSP Practice with SecurityScorecard MAX
Managing vendor security is a growing challenge for MSPs. Clients expect you to deliver enterprise-grade protection across their entire supply chain. However, many struggle with limited resources, manual processes, and the complexity of addressing third-party risks. SecurityScorecard MAX turns this challenge into an opportunity, helping you protect your clients while driving recurring revenue for your business.