Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2022
What Does Defense-in-depth Mean and How Does it Bring Infrastructure and Data Security Together?
With the rise of ransomware and cyber attacks, the term defense-in-depth has risen to the forefront, but what exactly does it mean? At its core, defense-in-depth is a protection mechanism for network security–an approach that involves layering or using multiple controls in series to protect against possible threats. This layered concept provides multiple redundancies in the event systems and data are compromised.
Ransomware: 2023's top attacks and need-to-know stats
As we navigate through 2023, ransomware attacks continue to grow in scale and sophistication. This year has already witnessed an alarming number of high-profile incidents (at the time of writing), meaning ransomware attacks remain one of the most significant cybersecurity threats organizations face.
How to Decrypt Ransomware (with 100% Free Tools)
Ransomware attacks are dominating news headlines, with ransomware-as-a-service (RaaS) operators actively seeking to exploit network vulnerabilities and infect unsuspecting victims. The healthcare sector and financial industry are especially vulnerable to ransomware attacks, as they store valuable personally identifiable data (PII) which can be misused to carry out lucrative crimes, like identity theft and fraud.
Emotet Analysis: New LNKs in the Infection Chain - The Monitor, Issue 20
Kroll has been tracking Emotet since it was first identified in 2014, especially during its transition from a banking Trojan designed to primarily steal credentials and sensitive information to a multi-threat polymorphic downloader for more destructive malware. Today, Emotet operators stand as one of the most prominent initial access brokers, providing cybercriminals with access to organizations for a fee.
The Aftermath: Steps to Recovering from a Malware Attack
Rapidly evolving IoT malware EnemyBot now targeting Content Management System servers and Android devices
AT&T Alien Labs™ has been tracking a new IoT botnet dubbed “EnemyBot”, which is believed to be distributed by threat actor Keksec. During our investigations, Alien Labs has discovered that EnemyBot is expanding its capabilities, exploiting recently identified vulnerabilities (2022), and now targeting IoT devices, web servers, Android devices and content management system (CMS) servers.
Ransomware demands acts of kindness to get your files back
The great thing about working in the world of cybersecurity is that there’s always something new. You may think you’ve seen it all, and then something comes along that completely surprises you. And that’s certainly true of the GoodWill ransomware, which security firm CloudSEK described this week.
Grandoreiro Banking Malware Resurfaces for Tax Season
Trustwave SpiderLabs in early April observed a Grandoreiro malware campaign targeting bank users from Brazil, Spain, and Mexico. The campaign exploits the tax season in target countries by sending out tax-themed phishing emails. Grandoreiro was first detected in 2016 is one of the largest banking trojan families developed to strike targets Latin America.
How Defenders Can Hunt for Malicious JScript Executions: A Perspective from OverWatch Elite
An adversary’s ability to live off the land — relying on the operating system’s built-in tooling and user-installed legitimate software rather than tooling that must be brought in — may allow them to navigate through a victim organization’s network relatively undetected. CrowdStrike Falcon OverWatch™ threat hunters are acutely aware of adversaries’ love of these living off the land binaries (LOLBins) and build their hunts accordingly.
Hunting a Global Telecommunications Threat: DecisiveArchitect and Its Custom Implant JustForFun
The New RansomHouse on The Block
Mirai Malware Variants for Linux Double Down on Stronger Chips in Q1 2022
Popular for compromising internet-connected devices and conducting distributed denial of service (DDoS) attacks, Mirai malware variants have been known to compromise devices that run on Linux builds ranging from mobile and Internet of Things (IoT) devices to cloud infrastructures.
Threat Update: AcidRain Wiper
The Splunk Threat Research Team has addressed a new malicious payload named AcidRain. This payload, deployed in the ongoing conflict zone of Eastern Europe, is designed to wipe modem or router devices (CPEs).
Q1 2022 Threat Landscape: Threat Actors Target Email for Access and Extortion
In Q1 2022, Kroll observed a 54% increase in phishing attacks being used for initial access in comparison with Q4 2021. Email compromise and ransomware were the two most common threat incident types, highlighting the integral part played by end users in the intrusion lifecycle.
Coffee Talk with SURGe: 2022-MAY-17 Conti Hits Costa Rica, Cardiologist Ransomware, CISA MSP Alert
Monitoring Data Risks & Investigating Threats Faster With the Rubrik Data Observability Engine
Why is it that the most impressive technologies are often the ones that go unnoticed? Sometimes what makes technology impressive is precisely that it goes unnoticed, and that is the case with the Rubrik Data Observability engine. As ransomware continues to grow as a real, costly, and persistent threat to conducting business, organizations are looking for smarter and faster ways to keep data safe and recover easily in the face of cyber attacks.
Become Unstoppable with the Rubrik Data Security Command Center
From technology to healthcare to governments, ransomware is disrupting business like never before. Security teams are reevaluating their overall security posture and taking additional measures to secure their data. During this process, they are discovering that they don’t know if their organization’s data is fully secure and whether it will be available when they need it.
Stronger Cybersecurity, Thanks to the New Rubrik Security Cloud
Sad fact: cyberattacks continue to grow in volume and sophistication. Plus, ransomware doesn't hit like a bomb–it’s often more like a Trojan Horse, where many organizations don't realize they are under attack until it's too late. Despite investments in infrastructure security tools deployed at the endpoint, perimeter, and network, bad actors are still getting through to hold data for ransom.
Threat Containment: Contain the Threats, Recover the Data
A common mistake made in responding to ransomware is rushing through a recovery only to realize that the recovery point was a compromised copy of the system, and in turn, re-introduces the threat back into the environment. To make matters worse, if a replicated copy were to be recovered at a tertiary site, it might introduce malware into networks that it previously didn’t have access to and further impact business operations.
Demo: WatchGuard ThreatSync - Live Malware, Known and Unknown
Ransomware Attacks: How They Happen, the Threats and Risks
Ransomware attacks are on the rise, and businesses need to be aware of the dangers they pose. In this blog post, we will discuss how ransomware attacks take place, the threats they pose, and the aftermath for businesses. We will also provide tips for protecting your business from ransomware attacks. If you prefer a watch over a read, our consultant breaks Ransomware down in the video below.
TechBites - Ransomware Explained
Stories from the SOC - Persistent malware
One of the most prevalent threats today, facing both organizations and individuals alike, is the use of ransomware. In 2021, 37% of organizations said they were victims of some type of ransomware attack. Ransomware can render large amounts of important data inaccessible nearly instantly. This makes reacting to potential ransomware events in a timely and accurate manner extremely important. Utilizing an endpoint security tool is critical to help mitigate these threats.
Two Minutes of Ransomware Attacks: The Facts
In this blog post, we will discuss what ransomware is, how it is used and the risks associated with it. We will also provide tips on how to protect yourself from ransomware attacks. If you prefer to watch Liam explain Ransomware in two minutes, click here.
How to Create a Ransomware Defense Strategy
How do organizations protect against ransomware? You need a ransomware defense strategy. It's important to find the best ransomware defense strategy that is right for your organization. Here are several facts about ransomware to help protect your organization.
Follow the Money: How eCriminals Monetize Ransomware
The transaction details and monetization patterns of modern eCrime reveal critical insights for organizations defending against ransomware attacks. Cybercrime has evolved over the past several years from simple “spray and pray” attacks to a sophisticated criminal ecosystem centered around highly effective monetization techniques that enable adversaries to maximize success and profitability.
CrowdStrike Falcon Pro for Mac Achieves Highest Score in AV-TEST MacOS Evaluation for Business Users (March 2022)
CrowdStrike is the only vendor to achieve the highest possible score of 18 points in protection, performance and usability out of all four tested vendors during the AV-TEST MacOS evaluation for business users in March 2022.
RedLine Stealer Campaign Using Binance Mystery Box Videos to Spread GitHub-Hosted Payload
RedLine Stealer is a malware that emerged in 2020, discovered in underground forums being sold in different plans, starting from $100 per month. The malware offers many capabilities for device reconnaissance, remote control, and information stealing, including: Since its discovery, attackers have used many different vectors to spread this stealer, including through fake installers and fake game hacking tools. Also, RedLine Stealer was found in compromised devices by the DEV-0537 hacking group (a.k.a.
Why Hackers Are Targeting Microsoft 365
It’s no secret that hackers are attracted to large and lucrative targets in the vast digital sphere. Oftentimes, the largest targets present the most avenues for attack. And with over 300 million users worldwide, Microsoft 365 is one of those large targets. Over 80% of deployed Microsoft 365 accounts have suffered an email breach and over 70% have suffered an account takeover.
SecureAge Technology launches CatchPulse software for complete protection against malware
Building Cyber Resiliency with the TCS-Rubrik Solution
Data is an integral part of any organization and hence it is important to respond to and recover it from any crisis. With the onset of the COVID-19 pandemic, the need for data security and cyber resiliency is evident. Cyber resiliency is the ability to prepare for, respond to, and recover from cyber-attacks and data breaches while continuing to operate effectively.
npm supply chain attack targets Germany-based companies with dangerous backdoor malware
The JFrog Security research team constantly monitors the npm and PyPI ecosystems for malicious packages that may lead to widespread software supply chain attacks. Last month, we shared a widespread npm attack that targeted users of Azure npm packages. Over the past three weeks, our automated scanners have detected several malicious packages in the npm registry, all using the same payload.
Emotet: The Return of the World's Most Dangerous Malware
In our new threat briefing report, Forescout’s Vedere Labs analyzes an Emotet sample, presents a list of IoCs extracted from the analysis and discusses mitigation. Emotet is the name of both a cybercrime group and a malware loader it distributes. The group is also known as MUMMY SPIDER, while the malware is also known as Geodo or Heodo.
Stories from the SOC - Command and Control
Once a malicious actor has gained initial access to an internal asset, they may attempt to conduct command and control activity.
How Do You Get Infected by Ransomware?
Over the last few years, the rate of cyberattacks has continued to hit record growth, taking advantage of individuals or businesses with poor cybersecurity practices. These attacks have affected healthcare, government, finance, and major businesses around the world. Of these cyberattacks, ransomware consistently ranks at the top of the most common cyber threats list, with an estimated 623 million incidents worldwide in 2021.
What Is Ransomcloud?
Tech decision makers surveyed by Pulse admitted last year that nearly 3 out of 4 companies (71%) experienced a ransomware incident and at least 12% of these incidents involved payments. This shows that ransomware attacks are proving to be a lucrative business for malicious cyber actors as they constantly put organizations’ cybersecurity measures to the test in a host of different sectors where different IT architectures are used.
Emotet: New Delivery Mechanism to Bypass VBA Protection
Emotet started as a banking trojan in 2014 and later evolved to what has been considered the world’s most dangerous malware by Europol, often used throughout the world to deliver many different threats, including TrickBot. In October 2020, Netskope analyzed an Emotet campaign that was using PowerShell and WMI within malicious Office documents to deliver its payload. Later in 2021, we also spotted new delivery mechanisms being used, including squiblytwo.
Deep dive on the BLISTER loader
Yesterday, the Elastic Security Research Team released a detailed report outlining technical details regarding the BLISTER launcher, a sophisticated campaign that we uncovered in December 2021. This latest release continues on research we’ve developed while observing the campaign over the last few months — specifically pertaining to the technical details of how the group behind this payload is able to stay under the radar and evade detection for many new samples identified.
macOS Malware Is More Reality Than Myth: Popular Threats and Challenges in Analysis
Understanding the threat landscape and how threats behave is the first step CrowdStrike researchers take toward strengthening customer protection. They based the following threat landscape analysis on internal and open source data, which revealed that in 2021 the most commonly encountered macOS malware types were ransomware (43%), backdoors (35%) and trojans (17%). Each category is powered by a different motive: ransomware by money, backdoors by remote access and trojans by data theft. Figure 1.
Achieve Near-Zero RPO & RTO with Orchestrated Application Recovery
In the summer of 2021, Rubrik officially released its first SaaS-based automated Disaster Recovery (DR) solution, Orchestrated Application Recovery. Orchestrated Application Recovery is incredibly easy to use: no need to install new binaries, no need to integrate between different vendor’s products.
Threat Update: Cyclops Blink
The Splunk Threat Research Team continues to address ongoing threats in relation to geopolitical events in eastern Europe. The following payload named Cyclops Blink seems to target Customer Premise Equipment devices (CPE). These devices are generally prevalent in commercial and residential locations enabling internet connectivity (Cable, DSL Modems, Satellite Modems, Firewalls, etc).
BlackCat/ALPHV Ransomware: Cybriant Responds to FBI Warning
The Federal Bureau of Investigation (FBI) recently released a Flash Report regarding BlackCat Ransomware breaches. This ransomware as a service (RaaS) has compromised at least 60 entities worldwide and is the first ransomware group to do so successfully using RUST, considered to be a more secure programming language that offers improved performance and reliable concurrent processing.
TechBites - The Threat of Ransomware
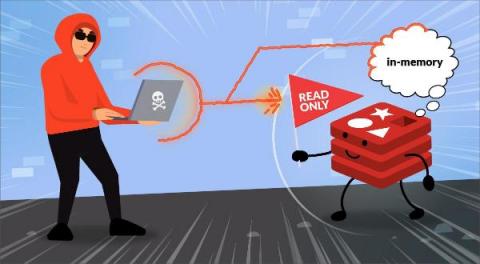
Compromising Read-Only Containers with Fileless Malware
Containers provide a number of security features that are not simply available on a normal host. One of those is the ability to make the container’s root filesystem read-only. By making the file system unable to be altered, it prevents an attacker from writing their malware executable to disk. Most attacks rely on writing files in order to work, but sophisticated cases use fileless malware as part of their malicious behavior.
Ransomware Response and Remediation With a Data Observability Engine for Data Security
Ransomware can be expensive—in 2021, the average cost of a ransomware attack was $4.62million, and that doesn’t include the ransom itself. Beyond financial costs, the cost of time, data, and brand reputation can also be astronomical. According to the IST Ransomware Task Force, the average downtime can be 21 days, with full recovery taking on average 287 days from the initial ransomware incident response. And cyber criminals are getting more sophisticated every year.
Analysis on recent wiper attacks: examples and how wiper malware works
Wiper’s main objective is to destroy data from any storage device and make the information unavailable (T1485). There are two ways of removing files, logical and physical. Logical file removal is the most common way of erasing a file, performed by users daily when a file is sent to (and emptied from) the Recycle bin, or when it is removed with the command line or terminal with the commands del/rm.
AWS Targeted by a Package Backfill Attack
On April 28 and April 30, respectively, WhiteSource Diffend identified, blocked, and reported two packages we deemed were malicious versions of original Amazon Web Services (AWS) packages. Whitesource security experts have reached out to contacts at Amazon to notify them of our findings. This discovery may point to a new takeover method that targets packages of well-known origins, in this case, AWS.