How To Prevent Account Takeover Attacks
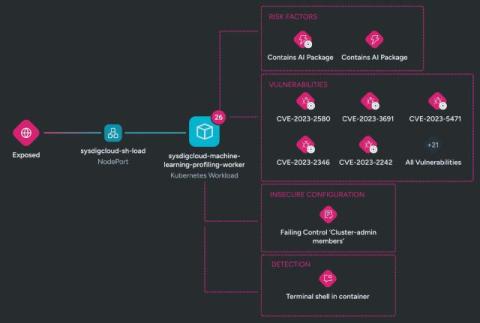
An account takeover attack is a type of identity theft that occurs when a cybercriminal gains access to your online account and changes your login credentials to lock you out. Once you cannot log back in, a cybercriminal will use your identity to steal private information or even scam others. You can prevent account takeover attacks by using strong passwords, enabling Multi-Factor Authentication (MFA) and investing in dark web monitoring.