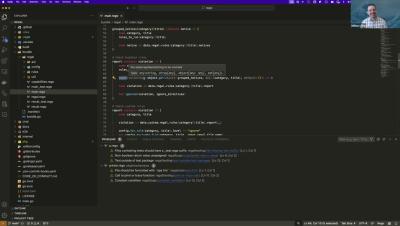
Tooltips and inlay hints for the OPA VS Code extension, powered by Regal
Our DevRel guru Anders Eknert, and our eminent VP of Marketing, William Chia, talk about two new features in the OPA extension for VS Code — tooltips and inlay hints for built-in functions. Both provided by Styra's linter and language server for Rego, Regal.