Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
5 Things to Do Immediately After Your Startup Is the Victim of a Cyber Attack
Stats suggest that 43% of cyber attacks target small businesses and 60% of these attacks are encountered within the first 6 months of setting up a business. While the horrors of cyber attacks are known to everyone, getting such a fatal blow right when you are starting, can send your startup on a trip to Bermuda Triangle! However, proper planning and having a reliable security strategy can help you bring back from the place of no return!
Snyk Open Source adds beta C/C++ security scanning for unmanaged OSS
We’re happy to announce the open beta of C/C++ security scanning in Snyk Open Source, enabling development and security teams to find and fix known security vulnerabilities in their C/C++ open source code and libraries! Used across various industry verticals and prominent within the gaming, hardware/IoT, and communications industries, C/C++ continues to have a major impact on software development and the technology space as a whole.
The Top Cyber Attacks of November 2021
6 Common Hacking Techniques and How to Avoid Them
According to the recent Verizon Data Breach Investigations report, 45% of breaches featured hacking in 2020. With high-value information such as user credentials and credit card information being stored on personal devices and transmitted freely online, hacking techniques have evolved to become more sophisticated than ever before.
Snyk Customer Story: ActiveCampaign
Jailbreaking an iPhone: Should you Jailbreak yours?
The technical term jailbreaking implies that a locked-down electronic device has been changed to remove restrictions and allow the installation of unauthorised software. Although the term contains breaking, it doesn’t involve breaking anything physically.
What is Security as a Service? Advantages and Use of SECaas
Cyber security is a serious concern for businesses in the digital age. It is not uncommon these days to see businesses spending big amounts on security solutions that are difficult to maintain and even more expensive to upgrade. For this reason, security as a service (SECaaS) has gained traction because it allows businesses to outsource their security needs reliably without having to go through the hassle of investing in resources and solutions.
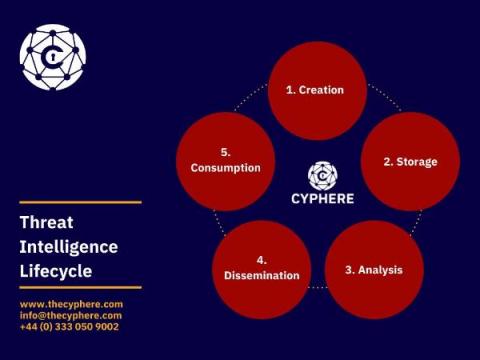
Threat Intelligence: Everything You Need to Know
This blog post will discuss the definition of threat intelligence and different stages of the threat intelligence cycle to help you better understand what happens behind the scenes.