What is Metasploit?
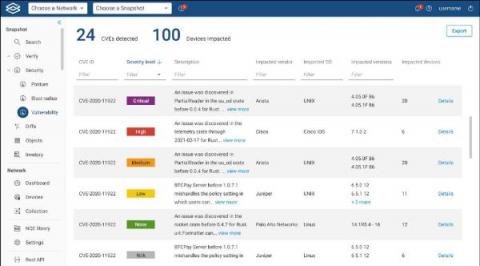
The Metasploit Framework is a Ruby-based, open-source framework that is used by information security professionals and cybercriminals to find, exploit, and validate system vulnerabilities. The framework consists of various exploitation tools and penetration testing tools. Information security teams most commonly use Metasploit for penetration testing (or “ethical hacking”) to identify and remediate any existing vulnerabilities across an organization’s networks.